关于Android中Failedtoreadkeyfromkeystore解决办法和androidfailedtoresolve的问题就给大家分享到这里,感谢你花时间阅读本站内容,更多关于"Faile
关于Android 中Failed to read key from keystore解决办法和android failed to resolve的问题就给大家分享到这里,感谢你花时间阅读本站内容,更多关于"Failed to execute tools\android.bat"解决办法、aes – <4.3的Android KeyStore实现、Android Eclipse keystore.jks文件生成,根据keystore密钥获取SHA1安全码 ,apk打包、Android Gradle Build Error:Some file crunching failed, see logs for details解决办法等相关知识的信息别忘了在本站进行查找喔。
本文目录一览:- Android 中Failed to read key from keystore解决办法(android failed to resolve)
- "Failed to execute tools\android.bat"解决办法
- aes – <4.3的Android KeyStore实现
- Android Eclipse keystore.jks文件生成,根据keystore密钥获取SHA1安全码 ,apk打包
- Android Gradle Build Error:Some file crunching failed, see logs for details解决办法

Android 中Failed to read key from keystore解决办法(android failed to resolve)
Android 中Failed to read key from keystore解决办法
Caused by: org.gradle.tooling.BuildException: Failed to read key from keystore
at com.android.build.gradle.tasks.PackageApplication.doFullTaskAction(PackageApplication.groovy:110)
at com.android.build.gradle.internal.tasks.IncrementalTask.taskAction(IncrementalTask.groovy:64)
at org.gradle.internal.reflect.JavaMethod.invoke(JavaMethod.java:63)
at org.gradle.api.internal.project.taskfactory.AnnotationProcessingTaskFactory$IncrementalTaskAction.doExecute(AnnotationProcessingTaskFactor
y.java:235)
at org.gradle.api.internal.project.taskfactory.AnnotationProcessingTaskFactory$StandardTaskAction.execute(AnnotationProcessingTaskFactory.jav
a:211)
at org.gradle.api.internal.project.taskfactory.AnnotationProcessingTaskFactory$IncrementalTaskAction.execute(AnnotationProcessingTaskFactory.
java:222)
at org.gradle.api.internal.project.taskfactory.AnnotationProcessingTaskFactory$StandardTaskAction.execute(AnnotationProcessingTaskFactory.jav
a:200)
at org.gradle.api.internal.tasks.execution.ExecuteActionsTaskExecuter.executeAction(ExecuteActionsTaskExecuter.java:80)
at org.gradle.api.internal.tasks.execution.ExecuteActionsTaskExecuter.executeActions(ExecuteActionsTaskExecuter.java:61)
... 47 more
Caused by: com.android.builder.packaging.SigningException: Failed to read key from keystore
at com.android.builder.core.AndroidBuilder.packageApk(AndroidBuilder.java:1468)
at com.android.builder.core.AndroidBuilder$packageApk$6.call(UnkNown Source)
at com.android.build.gradle.tasks.PackageApplication.doFullTaskAction(PackageApplication.groovy:95)
... 55 more
build.gradle
signingConfigs {
robert {
storePassword 'robert'
storeFile file('/Users/bournewang/Documents/Project/android.keystore')
keyPassword 'robert'
keyAlias 'mike'
}
}
解决方案:
Check your keystore file for first,in you example you creating file with name my-release-key.keystore. If its correct and really present in folder Users/bournewang/Documents/Project check alias,in your example it is -alias alias_name,but in config you specified alias mike
大意是:
1.android.keystore可能不在指定目录下面
2.keyAlias不对
另:想知道真正原因的话,可以查看
To find out what's wrong you can use gradle's singingReport command. On mac: ./gradlew signingReport On Windows: gradle signingReport
如有疑问请留言或者到本站社区交流讨论,感谢阅读,希望能帮助到大家,谢谢大家对本站的支持!

"Failed to execute tools\android.bat"解决办法
一、问题
配置Android开发环境过程中,需安装Android SDK。打开SDK Manager.exe,发生如下错误:
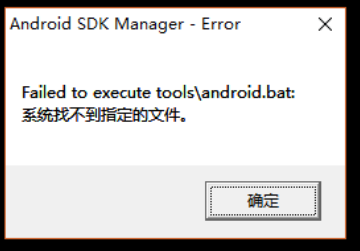
二、解决方法
在文件夹temp中找到“ tools_r25.2.2-windows.zip ”,并将其解压覆盖tool文件夹。
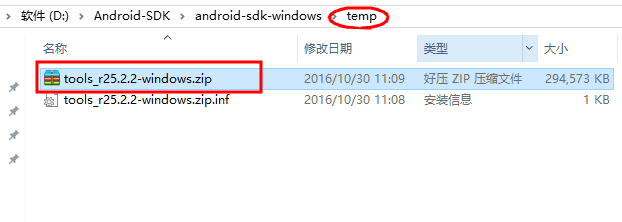
再次打开SDK Manager.exe就不会报错了。

aes – <4.3的Android KeyStore实现
我打算在我的Android应用程序中使用KeyStore,使用存储在KeyStore中的KeyPair加密AES密钥. KeyStore的Android文档:
https://developer.android.com/training/articles/keystore.html
在搜索互联网后,我找到了一个AOSP示例,我编辑了这个:
/*
* copyright (C) 2013 The Android Open Source Project
*
* Licensed under the Apache License, Version 2.0 (the "License");
* you may not use this file except in compliance with the License.
* You may obtain a copy of the License at
*
* http://www.apache.org/licenses/LICENSE-2.0
*
* Unless required by applicable law or agreed to in writing, software
* distributed under the License is distributed on an "AS IS" BASIS,
* WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
* See the License for the specific language governing permissions and
* limitations under the License.
*/
import android.annotation.TargetApi;
import android.content.Context;
import android.os.Build;
import android.security.KeyPairGeneratorSpec;
import java.io.IOException;
import java.math.BigInteger;
import java.security.GeneralSecurityException;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.KeyStore;
import java.security.KeyStoreException;
import java.security.NoSuchAlgorithmException;
import java.security.UnrecoverableEntryException;
import java.util.Calendar;
import java.util.GregorianCalendar;
import javax.crypto.Cipher;
import javax.crypto.SecretKey;
import javax.security.auth.x500.X500Principal;
/**
* Wraps {@link SecretKey} instances using a public/private key pair stored in
* the platform {@link KeyStore}. This allows us to protect symmetric keys with
* hardware-backed crypto, if provided by the device.
* <p>
* See <a href="http://en.wikipedia.org/wiki/Key_Wrap">key wrapping</a> for more
* details.
* <p>
* Not inherently thread safe.
*
* Some explanations:
* http://nelenkov.blogspot.nl/2013/08/credential-storage-enhancements-android-43.html
*/
public class SecretKeyWrapper {
private final Cipher mCipher;
private final KeyPair mPair;
/**
* Create a wrapper using the public/private key pair with the given alias.
* If no pair with that alias exists, it will be generated.
*/
public SecretKeyWrapper(Context context, String alias)
throws GeneralSecurityException, IOException {
mCipher = Cipher.getInstance("RSA/ECB/PKCS1Padding");
final KeyStore keyStore = KeyStore.getInstance("AndroidKeyStore");
keyStore.load(null);
if (!keyStore.containsAlias(alias)) {
generateKeyPair(context, alias);
}
// Even if we just generated the key, always read it back to ensure we
// can read it successfully.
final KeyStore.PrivateKeyEntry entry = (KeyStore.PrivateKeyEntry) keyStore.getEntry(
alias, null);
mPair = new KeyPair(entry.getCertificate().getPublicKey(), entry.getPrivateKey());
}
@TargetApi(Build.VERSION_CODES.JELLY_BEAN_MR2)
private static void generateKeyPair(Context context, String alias)
throws GeneralSecurityException {
final Calendar start = new GregorianCalendar();
final Calendar end = new GregorianCalendar();
end.add(Calendar.YEAR, 100);
final KeyPairGeneratorSpec spec = new KeyPairGeneratorSpec.Builder(context)
.setAlias(alias)
.setSubject(new X500Principal("CN=" + alias))
.setSerialNumber(BigInteger.ONE)
.setStartDate(start.getTime())
.setEndDate(end.getTime())
.build();
final KeyPairGenerator gen = KeyPairGenerator.getInstance("RSA", "AndroidKeyStore");
gen.initialize(spec);
gen.generateKeyPair();
}
/**
* Wrap a {@link SecretKey} using the public key assigned to this wrapper.
* Use {@link #unwrap(byte[])} to later recover the original
* {@link SecretKey}.
*
* @return a wrapped version of the given {@link SecretKey} that can be
* safely stored on untrusted storage.
*/
public byte[] wrap(SecretKey key) throws GeneralSecurityException {
mCipher.init(Cipher.WRAP_MODE, mPair.getPublic());
return mCipher.wrap(key);
}
/**
* Unwrap a {@link SecretKey} using the private key assigned to this
* wrapper.
*
* @param blob a wrapped {@link SecretKey} as prevIoUsly returned by
* {@link #wrap(SecretKey)}.
*/
public SecretKey unwrap(byte[] blob) throws GeneralSecurityException {
mCipher.init(Cipher.UNWRAP_MODE, mPair.getPrivate());
return (SecretKey) mCipher.unwrap(blob, "AES", Cipher.SECRET_KEY);
}
}
这个实现可以包装和解包一个SecretKey,在我的情况下是一个AES密钥.
但是,此KeyStore仅在4.3及更高版本中受支持.请参阅Jelly Bean注释.
提出我的问题,同样实施4.3以下的可能性有哪些?
提前致谢,
解决方法:
密钥库从1.6开始提供,但早期版本中没有官方API.您仍然可以通过私有API使用它,但您可能会遇到各种问题.
可以在您引用的同一博客上找到一个示例:
http://nelenkov.blogspot.com/2012/05/storing-application-secrets-in-androids.html
实现可能最终有些棘手,因为密钥库需要独立于设备锁屏解锁.对于早期版本考虑基于密码的加密可能更好,博客上有一篇关于它的帖子.

Android Eclipse keystore.jks文件生成,根据keystore密钥获取SHA1安全码 ,apk打包
keystore.jks文件生成,打包APK
选中项目右键-> Android Tools->Export Signed Application Package ,如图:
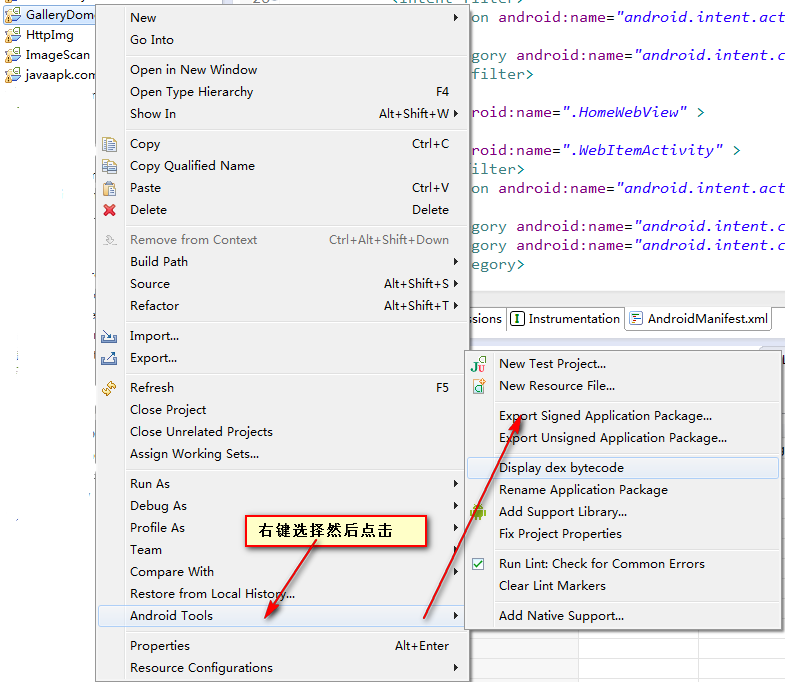
之后
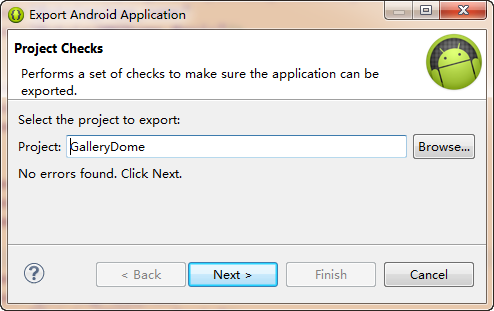
点击Next,下图 (建议文件名后缀为.keystore)
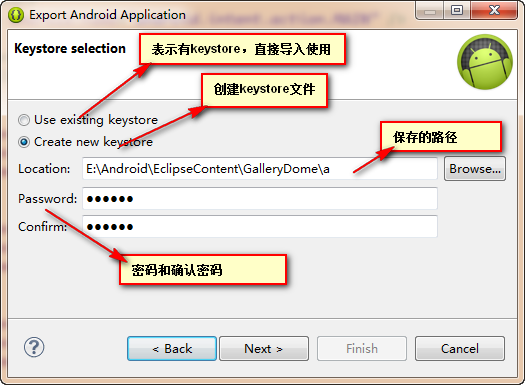
进入到”Key Creation“界面,完成信息,点击Next
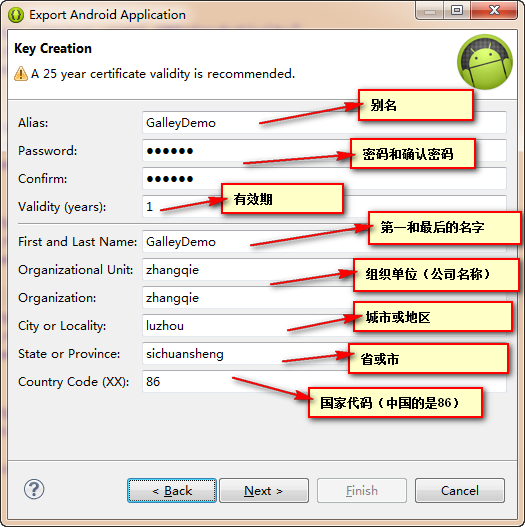
完成信息,(选择APK生成的路径)
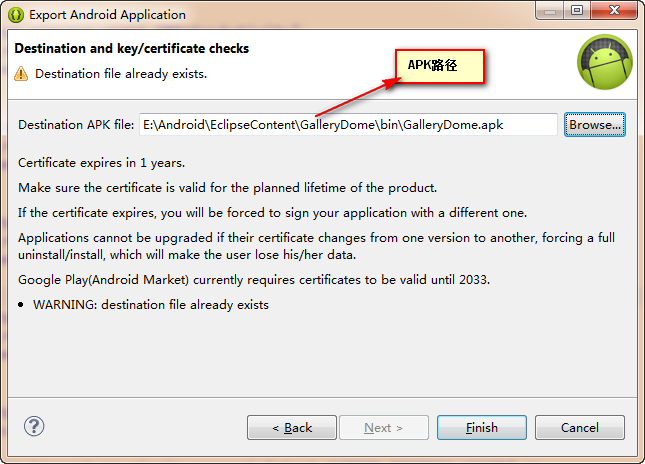
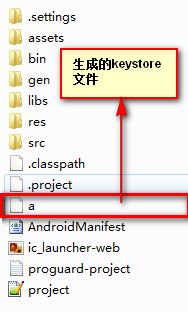
可以到保存路径下看生成的android.keystore文件了
接下来APK打包
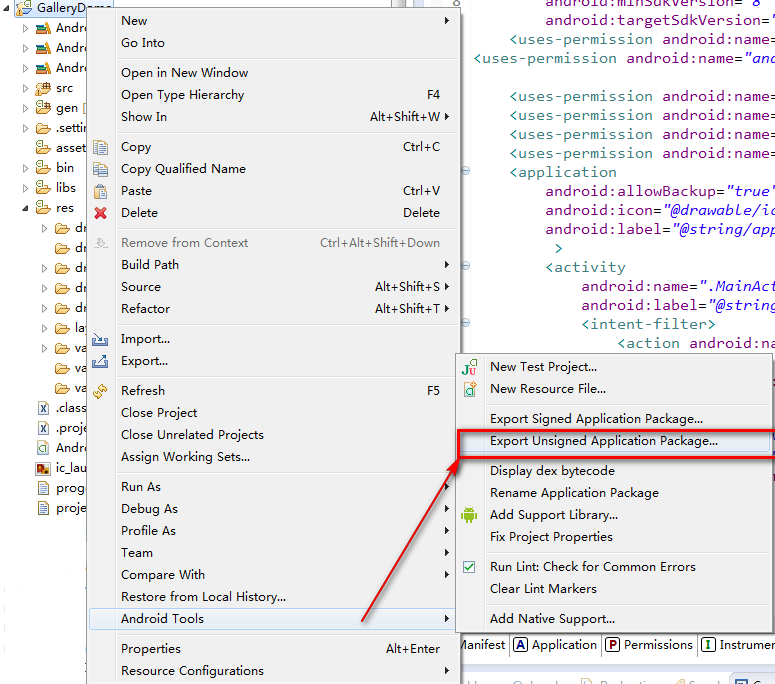
点击之后,选择保存路径:
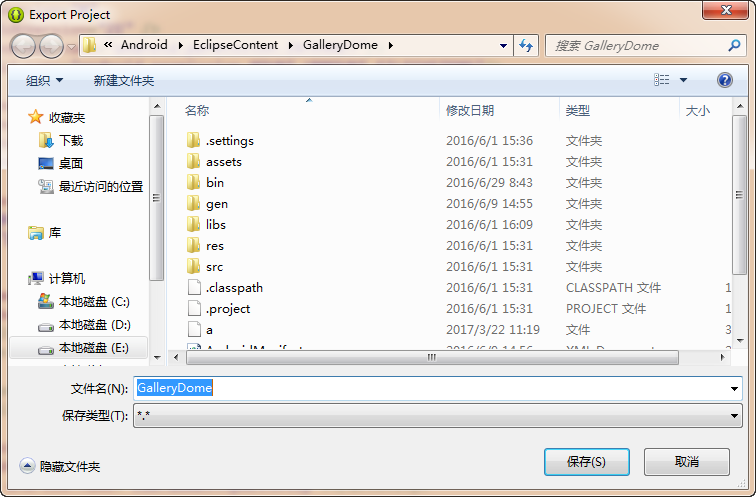
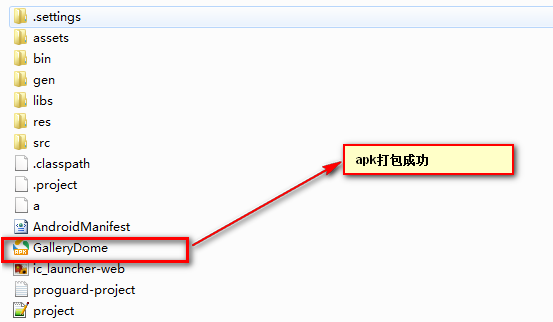
之后APK生成成功
根据keystore密钥获取SHA1安全码
通常做项目大多数都要用到SHA1安全码,比如:地图,获取SHA1安全码的也有两种,分为调试版和发布版,他们的SHA1都是不一样的,
debug测试版:
Window+R 打开控制台 输入cmd点击确定
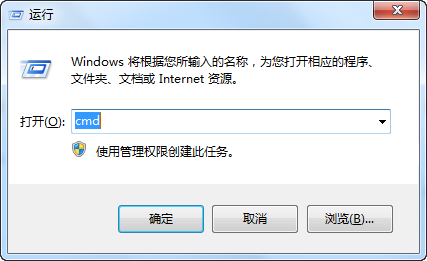
之后在弹框中完成以下操作就可以看到SHA1安全码了
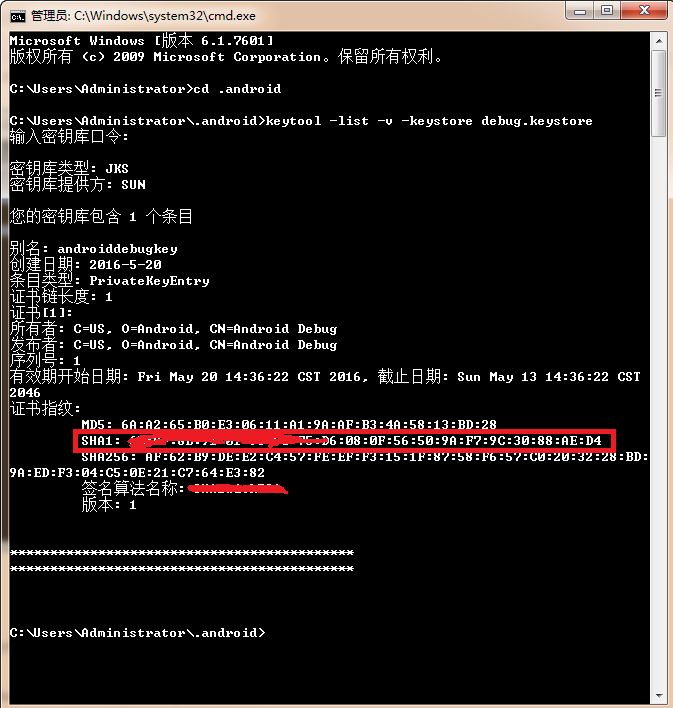
上图的密钥库口令默认的是:android (注:输入口令是看不见的,输入完成Enter即可)
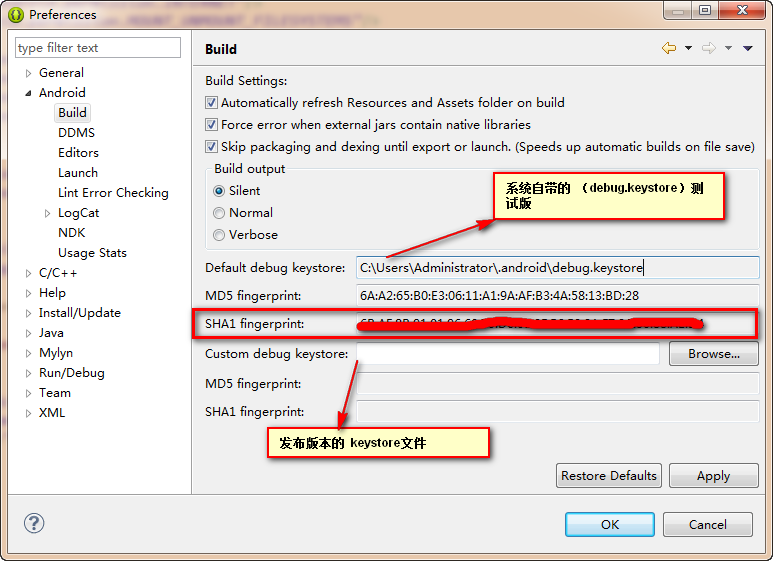
发布版(这个版本可以看到测试版和发布版的SHA1):
这个版本就需要我们前面生成的keystore文件了, Custom debug keystore:导入生成的keystore文件,点击Apply生成发布版本的密钥SHA1

Android Gradle Build Error:Some file crunching failed, see logs for details解决办法
在主工程文件夹下的build点gradle文件里,加两句:
aaptOptions点cruncherEnabled = false
aaptOptions点useNewCruncher = false
例如:
android {
compileSdkVersion 22
buildToolsVersion "23.0.1"
aaptOptions.cruncherEnabled = false
aaptOptions.useNewCruncher = false
defaultConfig {
minSdkVersion 5
targetSdkVersion 17
}
然后重新构建、运行
------------------------
2016.09.25 追加
如果
重启 android studio;
增加上述语句;
检查是否修改过文件后缀;
都不行,就试试升级 gradle。
今天关于Android 中Failed to read key from keystore解决办法和android failed to resolve的分享就到这里,希望大家有所收获,若想了解更多关于"Failed to execute tools\android.bat"解决办法、aes – <4.3的Android KeyStore实现、Android Eclipse keystore.jks文件生成,根据keystore密钥获取SHA1安全码 ,apk打包、Android Gradle Build Error:Some file crunching failed, see logs for details解决办法等相关知识,可以在本站进行查询。
本文标签:





