本文将带您了解关于computernetwork的新内容,同时我们还将为您解释computernetworks期刊的相关知识,另外,我们还将为您提供关于51nod1470计算机网络问题Codeforc
本文将带您了解关于computer network的新内容,同时我们还将为您解释computer networks期刊的相关知识,另外,我们还将为您提供关于51nod 1470 计算机网络问题 Codeforces Round #310 (Div. 1)E. Case of Computer Network、A Self-Organized Computer Virus Demo in C、CE235 Computer Security、CF555E Case of Computer Network的实用信息。
本文目录一览:- computer network(computer networks期刊)
- 51nod 1470 计算机网络问题 Codeforces Round #310 (Div. 1)E. Case of Computer Network
- A Self-Organized Computer Virus Demo in C
- CE235 Computer Security
- CF555E Case of Computer Network

computer network(computer networks期刊)
Internet,计算机网和分组交换
什么是协议(protocol)?为计算机网络中进行数据交换而建立的规则、标准或约定的集合。
面向终端的网络:
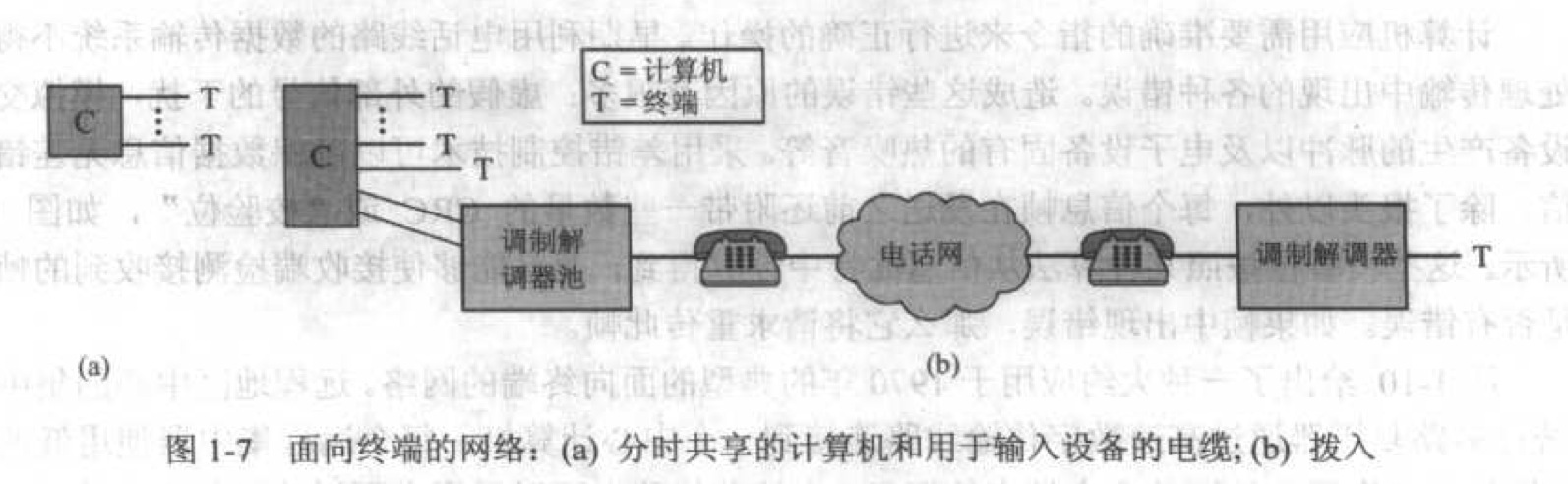
多个终端共享一台主机,每个终端通过电缆可以对主机进行远距离访问。通过引入用于传输数字信息的调制解调器(modem) 设备,终端可以通过电话网访问主机。
以下是几种不同的终端与主机间的通讯方式。
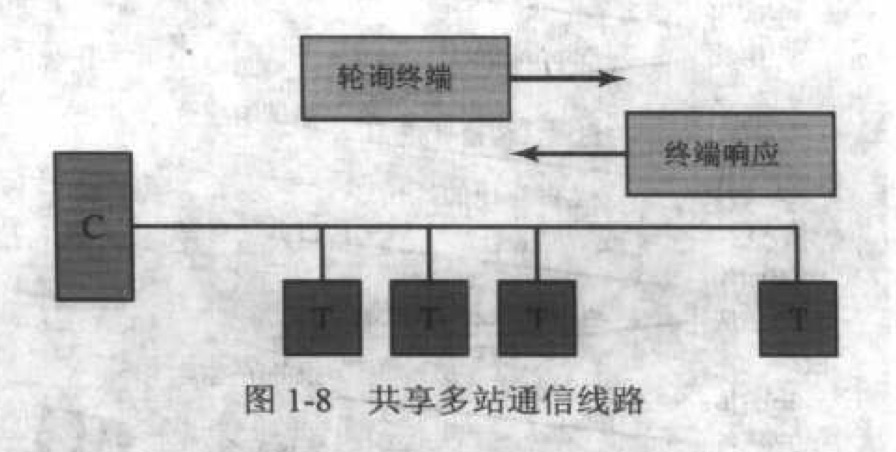
单线多点通信线路:中心计算机在输出线路上向某个特定的终端发送一个轮询消息,所有的终端都在监听此输出线路,但是只有 被轮询的终端进行响应。
统计多路复用器 / 集中器:来自多个终端的消息被多路复用器缓存,并排序在一个队列里,然后每次通过通信线路发送一个消息 到中心计算机。中心计算机分类出来各个终端的消息,进行必要的处理并在帧中返回结果。统计多路复用器利用帧中的地址来确 定目标终端。
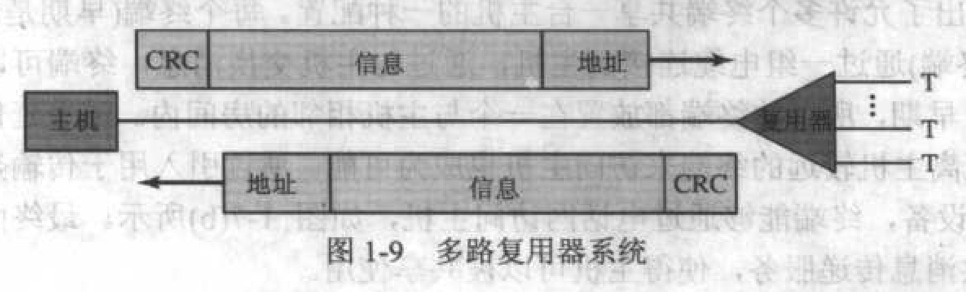
(CRC 是校验位,是按照某种算法从信息比特流中计算得到,并且能够使接收端检测接收到的帧中是否有错误,如果帧中出现 错误,那么它将请求重传此帧。)

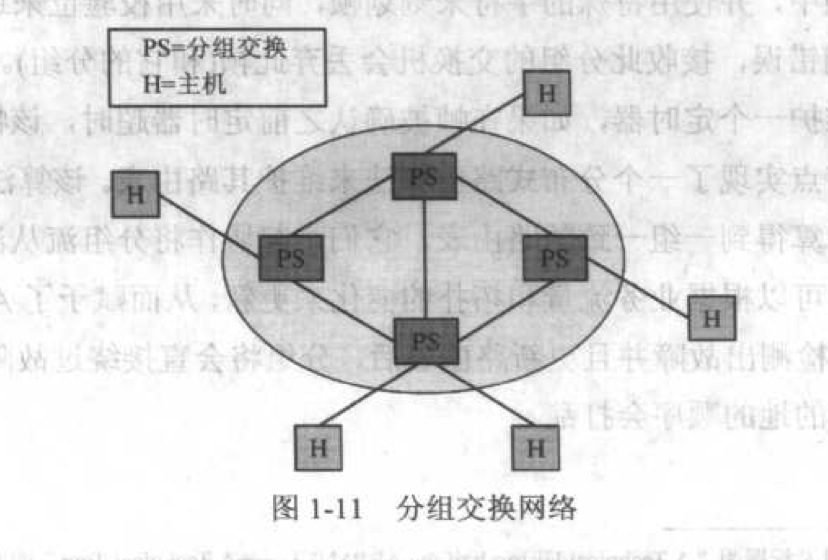
计算机到计算机的网络:
packet switching 解决了不同大小的消息进入网络带来的过长等待时间的问题。不能作为一个单独分组的消息将被分段, 然后使用多个分组进行传输。到达目标后再进行组装。

51nod 1470 计算机网络问题 Codeforces Round #310 (Div. 1)E. Case of Computer Network
总结
以上是小编为你收集整理的51nod 1470 计算机网络问题 Codeforces Round #310 (Div. 1)E. Case of Computer Network全部内容。
如果觉得小编网站内容还不错,欢迎将小编网站推荐给好友。

A Self-Organized Computer Virus Demo in C
A Program that can modify herself and copy herself to somewhere else and execute it. Just like gene-transformable virus.
Here''s the sample code.
#include "stdio.h"
#include "windows.h"
#define MAX_LOOP 10000
int main(int argc, const char** argv)
{
/*** THE VIRUS LOGIC PART ***/
//GENE_MARK
int a = 0;
printf("GENE PRINT:%d\n", a);
/*** THE VIRUS LOGIC PART ***/
// FILE NAME
char file_name[30] = "test";
// MAKE A COPY OF HERSELF
FILE* source = fopen("test.c", "r");
FILE* descendant = fopen("descendant.c", "w+");
printf("SOURCE FILE OPEN RESULT IS : %d \n", (int)source);
printf("DESCENDANT FILE CREATED: %d \n", (int)descendant);
if(descendant==NULL)
{
printf("ERROR ON CREATING DESCENDANT.\n");
return -1;
}
char buff[100] = {0};
// REPLACE GENE MARK PROGRAM
char letter = 0;
// GENE LINE
int idx = 0;
int loop = 0;
int buff_idx = 0;
while(!feof(source))
{
// ALARM
if(loop>MAX_LOOP)
break;
loop ++;
fread(&letter, sizeof(char), 1, source);
buff[buff_idx] = letter;
buff_idx ++;
if(letter==''\n'')
{
if(idx==9)
{
// TRANSFORM GENE
memset(buff, 0, 100);
buff_idx = 0;
strcat(buff, "int a = 1;\n");
}
fwrite(buff, sizeof(char), strlen(buff), descendant);
// CLEAR BUFFER
memset(buff, 0, 100);
buff_idx = 0;
idx ++;
}
}
// DEAL WITH LEFT LETTERS IN BUFFER
if(strlen(buff)>0)
{
strcat(buff, "\n");
fwrite(buff, sizeof(char), strlen(buff)+1, descendant);
}
// CLOSE ALL FILES
fclose(source);
fclose(descendant);
// until the descendant file is written over
/*** COMPILE HERSELF ***/
char* source_file = "descendant.c";
char* dest_file = "descendant.exe";
char command[100] = {0};
strcat(command, "gcc -o ");
strcat(command, dest_file);
strcat(command, " ");
strcat(command, source_file);
// COMPILATION
system(command);
/***********************/
printf("COPYING MYSELF DONE.\n");
printf("WAITING FOR NEXT INSTRUCTION...\n");
char cmd = getchar();
if(cmd==''Y'')
{
printf("BEGIN EXECUTE THE COPYFILE EXECUTION...\n");
//GENE_MARK
system("descendant.exe");
printf("EXECUTION PROCESS IS ACTIVATED, TASK DONE. EXIT SYSTEM.");
}
else
printf("YOU CHOOSE TO EXIT SYSTEM. BYE!");
return 0;
}If you have any suggestions or ideas, please feel free comment below, thanks!

CE235 Computer Security
CE235 Computer Security Assignment 3
The assignment is worth 7.5% of the total mark for this module. This assignment involves writing a C/C++ program for task 1 described below. The purpose of this assignment is for you to get a good understanding of the SHA-256.
The task:
Task 1 (7.5%)
Read the description and the pseudocode of SHA-256 at https://en.wikipedia.org/wiki/SHA-2 and develop the program called ConsoleSHA.cpp (which will be later renamed to CE235A3.cpp). Your program needs to be able to take an input and show the resulting hash value.
The program should contain brief comments describing the main block of the program, and the program should be laid out neatly with consistent indentation.
Assessment criteria:
Correctness of program 50%
Quality of program 25%
Clarity of program and comments 25%
Submission
You are required to submit the source code files (CE235A3.cpp). All of the files should be placed in a single folder which should then be zipped for submission to the coursework submission system (FASER), i.e. the submission should be a single file in zip format.
After you complete your programs, you should demonstrate them to the module supervisor.
Late submission and plagiarism
This assignment is to be done individually, i.e. whatever you submit must be your own individual work. Any software or any other materials that you use in this assignment, whether previously published or not, must be referred to and properly acknowledged. Please be aware that the module supervisor may ask students for an interview to explain their submitted work.
Please refer to the Undergraduate Students’ Handbook for details of the School policy regarding late submission and University regulations regarding plagiarism:
http://www.essex.ac.uk/ldev/resources/plagiarism/default.aspx
http://www.essex.ac.uk/about/governance/policies/academic-offences.aspx
因为专业,所以值得信赖。如有需要,请加 QQ:99515681 或 微信:codehelp

CF555E Case of Computer Network
传送门
题意
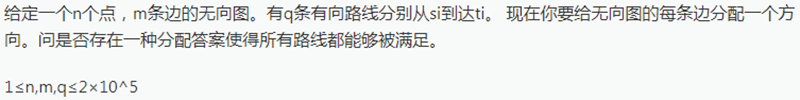
题解
容易发现,在同一个边双内的点我们是不用管它的,一定可以。
那么我们缩点,然后把图变成一颗树。这样,$s$ 到 $t$ 的路径就可以用$\mathrm{LCA}$求了。
我们把 $s$ 到 $\mathrm{LCA}$ 的路径打向上的标记,把 $\mathrm{LCA}$ 到 $t$ 的路径打向下的标记。
只要没有路径有两种标记,就是可以的。
打标记使用树上差分实现。时间复杂度:$\mathcal O\left(n+m+q\mathrm{lg}n\right)$。
附上代码:
#pragma GCC optimize(3)
#include <bits/stdc++.h>
using namespace std;
#define down(x, y) x = min(x, y)
int n, m, q;
struct edge {
int from, to, nxt, id;
} edges[400005];
struct edgE {
int to, nxt;
} edgEs[400005];
int e0, e = 1, e2 = 1, hed[200005], hEd[200005], tim = 0, fa[200005], dfn[200005], low[200005], scc[200005], dis[200005], lca[18][200005];
int flg[200005]; bool root[200005]; bool goon[200005];
int leaves[200005], top=0;
const int CLEAN_FLAG = 0x1;
const int UP_FLAG = 0x2;
const int DOWN_FLAG = 0x4;
stack<int> S;
inline bool hasflag(int x, int attr) {
return flg[x] & attr;
}
inline bool setflag(int x, int attr) {
if (attr == UP_FLAG && hasflag(x, DOWN_FLAG)) return false;
if (attr == DOWN_FLAG && hasflag(x, UP_FLAG)) return false;
flg[x] |= attr;
return true;
}
inline void addedge(int x, int y) {
edges[e] = (edge){x, y, hed[x], e2};
hed[x] = e++;
edges[e] = (edge){y, x, hed[y], e2++};
hed[y] = e++;
}
inline void addedgE(int x, int y) {
edgEs[e] = (edgE){y, hEd[x]};
hEd[x] = e++;
}
inline void _tarjan(int x) {
dfn[x] = low[x] = ++tim;
S.push(x);
for (int e=hed[x]; e; e=edges[e].nxt) {
int y = edges[e].to;
if (edges[e].id == fa[x]) continue;
if (!dfn[y]) {
fa[y] = edges[e].id;
_tarjan(y);
down(low[x], low[y]);
} else down(low[x], dfn[y]);
}
if (dfn[x] == low[x]) {
scc[x] = ++e2;
while (S.top() != x) {
scc[S.top()] = e2;
S.pop();
}
S.pop();
}
}
inline void tarjan() {
for (int i=1; i<=n; i++) if (!dfn[i]) _tarjan(i);
for (int i = 0; i < e0; i++) {
int x = edges[i].from, y = edges[i].to;
if (scc[x] == scc[y]) continue;
addedgE(scc[x], scc[y]);
}
}
inline void lca_pre() {
for (int i=1; i<18; i++)
for (int j=1; j<=n; j++)
lca[i][j] = lca[i-1][lca[i-1][j]];
}
inline int LCA(int x, int y) {
if (dis[x] > dis[y]) swap(x, y);
int u = dis[x], v = dis[y];
int X=x, Y=y;
for (int det = v-u, i=0; det; det>>=1, ++i)
if (det & 1) Y = lca[i][Y];
if (X == Y) return X;
for (int i=17; i>=0; i--) {
if (lca[i][X] == lca[i][Y]) continue;
X = lca[i][X]; Y = lca[i][Y];
}
return lca[0][X];
}
int group[200005], current;
inline void dfs(int x, int fa) {
bool isleaf = true; group[x] = current;
for (int e=hEd[x]; e; e=edgEs[e].nxt) {
int y = edgEs[e].to;
if (y != fa) {
isleaf = false;
lca[0][y] = x;
dis[y] = dis[x] + 1;
dfs(y, x);
}
}
if (isleaf) leaves[top++] = x;
}
inline bool akmachine(int x, int flag) {
while (!root[x]) {
if (goon[x]) return true;
goon[x] = true;
if (hasflag(x, UP_FLAG) && !hasflag(x, CLEAN_FLAG) && (flag & DOWN_FLAG)
|| hasflag(x, DOWN_FLAG) && !hasflag(x, CLEAN_FLAG) && (flag & UP_FLAG))
return false;
if (hasflag(x, CLEAN_FLAG)) flag = 0;
flag = flg[x] & (UP_FLAG | DOWN_FLAG);
x = lca[0][x];
}
return true;
}
inline bool check() {
for (int i=0; i<top; i++) if (!akmachine(leaves[i], 0)) return false;
return true;
}
inline bool solve() {
for (int i=1; i<=n; i++)
if (!dis[i]) {
current = i; lca[0][i] = i; root[i] = 1;
dfs(i, 0);
}
lca_pre();
while (q--) {
int s, t; cin >> s >> t;
s = scc[s]; t = scc[t];
if (group[s] != group[t]) return false;
if (s == t) continue;
int p = LCA(s, t);
if (p != s) if (!setflag(s, UP_FLAG)) return false;
if (p != t) if (!setflag(t, DOWN_FLAG)) return false;
setflag(p, CLEAN_FLAG);
}
return check();
}
int main() {
ios :: sync_with_stdio(false); cin.tie(0);
cin >> n >> m >> q;
for (int i=1; i<=m; i++) {
int x, y; cin >> x >> y;
addedge(x, y);
}
e0 = e; e = 1; e2 = 0; tarjan();
cout << (solve() ? "Yes" : "No") << endl;
return 0;
}关于computer network和computer networks期刊的问题就给大家分享到这里,感谢你花时间阅读本站内容,更多关于51nod 1470 计算机网络问题 Codeforces Round #310 (Div. 1)E. Case of Computer Network、A Self-Organized Computer Virus Demo in C、CE235 Computer Security、CF555E Case of Computer Network等相关知识的信息别忘了在本站进行查找喔。
本文标签:





