在这里,我们将给大家分享关于CE235ComputerSecurity的知识,同时也会涉及到如何更有效地3DComputerGrapihcsUsingOpenGL-18相机移动、ASelf-Organ
在这里,我们将给大家分享关于CE235 Computer Security的知识,同时也会涉及到如何更有效地3D Computer Grapihcs Using OpenGL - 18 相机移动、A Self-Organized Computer Virus Demo in C、An Introduction to Computer Thinking、Chapter 1: A Tour of Computer Systems的内容。
本文目录一览:- CE235 Computer Security
- 3D Computer Grapihcs Using OpenGL - 18 相机移动
- A Self-Organized Computer Virus Demo in C
- An Introduction to Computer Thinking
- Chapter 1: A Tour of Computer Systems
CE235 Computer Security
CE235 Computer Security Assignment 3
The assignment is worth 7.5% of the total mark for this module. This assignment involves writing a C/C++ program for task 1 described below. The purpose of this assignment is for you to get a good understanding of the SHA-256.
The task:
Task 1 (7.5%)
Read the description and the pseudocode of SHA-256 at https://en.wikipedia.org/wiki/SHA-2 and develop the program called ConsoleSHA.cpp (which will be later renamed to CE235A3.cpp). Your program needs to be able to take an input and show the resulting hash value.
The program should contain brief comments describing the main block of the program, and the program should be laid out neatly with consistent indentation.
Assessment criteria:
Correctness of program 50%
Quality of program 25%
Clarity of program and comments 25%
Submission
You are required to submit the source code files (CE235A3.cpp). All of the files should be placed in a single folder which should then be zipped for submission to the coursework submission system (FASER), i.e. the submission should be a single file in zip format.
After you complete your programs, you should demonstrate them to the module supervisor.
Late submission and plagiarism
This assignment is to be done individually, i.e. whatever you submit must be your own individual work. Any software or any other materials that you use in this assignment, whether previously published or not, must be referred to and properly acknowledged. Please be aware that the module supervisor may ask students for an interview to explain their submitted work.
Please refer to the Undergraduate Students’ Handbook for details of the School policy regarding late submission and University regulations regarding plagiarism:
http://www.essex.ac.uk/ldev/resources/plagiarism/default.aspx
http://www.essex.ac.uk/about/governance/policies/academic-offences.aspx
因为专业,所以值得信赖。如有需要,请加 QQ:99515681 或 微信:codehelp

3D Computer Grapihcs Using OpenGL - 18 相机移动
移动相机需要用到键盘按键,按键事件的引入需要包含头文件
#include <Qt3DInput\qkeyevent.h>
并实现 QWidget 中定义的虚函数 keyPressEvent
我们首先在 MyGlWindow 中重写这个虚函数。
在 MyGlWindow.h 加入
void keyPressEvent(QKeyEvent*);在 MyGlWindow.cpp 中定义:
1 void MyGlWindow::keyPressEvent(QKeyEvent * e)
2 {
3 switch (e->key())
4 {
5 case Qt::Key::Key_W:
6 camera.moveForward();
7 break;
8 case Qt::Key::Key_S:
9 camera.moveBackward();
10 break;
11 case Qt::Key::Key_A:
12 camera.strafeLeft();
13 break;
14 case Qt::Key::Key_D:
15 camera.strafeRight();
16 break;
17 case Qt::Key::Key_Q:
18 camera.moveUp();
19 break;
20 case Qt::Key::Key_E:
21 camera.moveDown();
22 break;
23
24 default:
25 break;
26 }
27 repaint();
28 }代码很简单,从中我们可以看到按下 W 和 S 键会分别前进、后退,按下 A 和 D 键会分别向左向右平移,按下 Q 和 E 键会分别向上向下平移。
但是目前我们还没有在 Camera 类中实现这 6 个移动的函数。
下面就来实现这些函数:
在 Camera.h 中添加成员:
1 void moveForward();
2 void moveBackward();
3 void strafeLeft();
4 void strafeRight();
5 void moveUp();
6 void moveDown();
7
8 float moveSpeed = 0.1f;在 Camera.cpp 中定义这些方法:
1 void Camera::moveForward()
2 {
3 position += viewDirection * moveSpeed;
4 }
5
6 void Camera::moveBackward()
7 {
8 position -= viewDirection * moveSpeed;
9 }
10
11 void Camera::strafeLeft()
12 {
13 glm::vec3 pitchAxis = glm::cross(viewDirection, UP);
14 position += pitchAxis * moveSpeed;
15 }
16
17 void Camera::strafeRight()
18 {
19 glm::vec3 pitchAxis = glm::cross(viewDirection, UP);
20 position -= pitchAxis * moveSpeed;
21
22 }
23
24 void Camera::moveUp()
25 {
26 position += UP * moveSpeed;
27 }
28
29 void Camera::moveDown()
30 {
31 position -= UP * moveSpeed;
32 }编译运行,我们发现相机可以前进后退上下左右平移了。
PS:
这里的上下并不是依照相机的局部坐标的上下,而是世界坐标的上下。要改成局部坐标的上下有些麻烦。
我做了一些尝试,定义一个新的成员 cameraUp,用来表示相机的上方,每次旋转过后都重新使用向量差乘来重新计算 cameraUp。这样确实可以按照相机的上下移动,但是带来了一些其他问题,相机在世界中不再是 “正” 的了,经过几次旋转,会累积一些偏差,导致相机倾斜。这里需要解决这个问题可能需要用到四元数,但是暂时不再深究了。

A Self-Organized Computer Virus Demo in C
A Program that can modify herself and copy herself to somewhere else and execute it. Just like gene-transformable virus.
Here''s the sample code.
#include "stdio.h"
#include "windows.h"
#define MAX_LOOP 10000
int main(int argc, const char** argv)
{
/*** THE VIRUS LOGIC PART ***/
//GENE_MARK
int a = 0;
printf("GENE PRINT:%d\n", a);
/*** THE VIRUS LOGIC PART ***/
// FILE NAME
char file_name[30] = "test";
// MAKE A COPY OF HERSELF
FILE* source = fopen("test.c", "r");
FILE* descendant = fopen("descendant.c", "w+");
printf("SOURCE FILE OPEN RESULT IS : %d \n", (int)source);
printf("DESCENDANT FILE CREATED: %d \n", (int)descendant);
if(descendant==NULL)
{
printf("ERROR ON CREATING DESCENDANT.\n");
return -1;
}
char buff[100] = {0};
// REPLACE GENE MARK PROGRAM
char letter = 0;
// GENE LINE
int idx = 0;
int loop = 0;
int buff_idx = 0;
while(!feof(source))
{
// ALARM
if(loop>MAX_LOOP)
break;
loop ++;
fread(&letter, sizeof(char), 1, source);
buff[buff_idx] = letter;
buff_idx ++;
if(letter==''\n'')
{
if(idx==9)
{
// TRANSFORM GENE
memset(buff, 0, 100);
buff_idx = 0;
strcat(buff, "int a = 1;\n");
}
fwrite(buff, sizeof(char), strlen(buff), descendant);
// CLEAR BUFFER
memset(buff, 0, 100);
buff_idx = 0;
idx ++;
}
}
// DEAL WITH LEFT LETTERS IN BUFFER
if(strlen(buff)>0)
{
strcat(buff, "\n");
fwrite(buff, sizeof(char), strlen(buff)+1, descendant);
}
// CLOSE ALL FILES
fclose(source);
fclose(descendant);
// until the descendant file is written over
/*** COMPILE HERSELF ***/
char* source_file = "descendant.c";
char* dest_file = "descendant.exe";
char command[100] = {0};
strcat(command, "gcc -o ");
strcat(command, dest_file);
strcat(command, " ");
strcat(command, source_file);
// COMPILATION
system(command);
/***********************/
printf("COPYING MYSELF DONE.\n");
printf("WAITING FOR NEXT INSTRUCTION...\n");
char cmd = getchar();
if(cmd==''Y'')
{
printf("BEGIN EXECUTE THE COPYFILE EXECUTION...\n");
//GENE_MARK
system("descendant.exe");
printf("EXECUTION PROCESS IS ACTIVATED, TASK DONE. EXIT SYSTEM.");
}
else
printf("YOU CHOOSE TO EXIT SYSTEM. BYE!");
return 0;
}If you have any suggestions or ideas, please feel free comment below, thanks!

An Introduction to Computer Thinking
1.Die Grundlage des Computers
1.1 Binärzahl in die Dezimalzahl umsetzen
Bereiten nach Gewicht,dann bekommen Summe
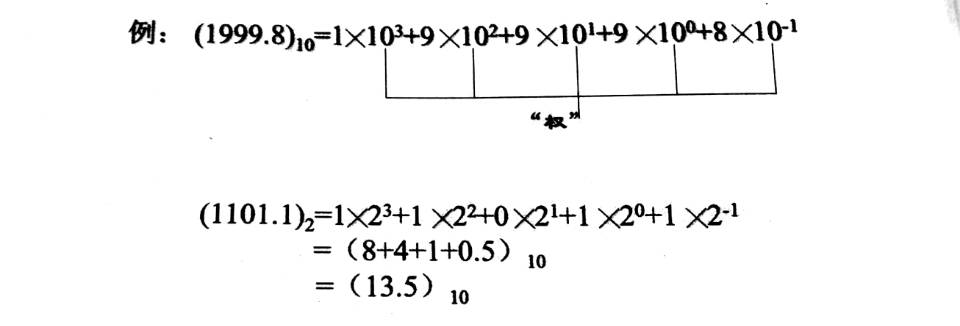
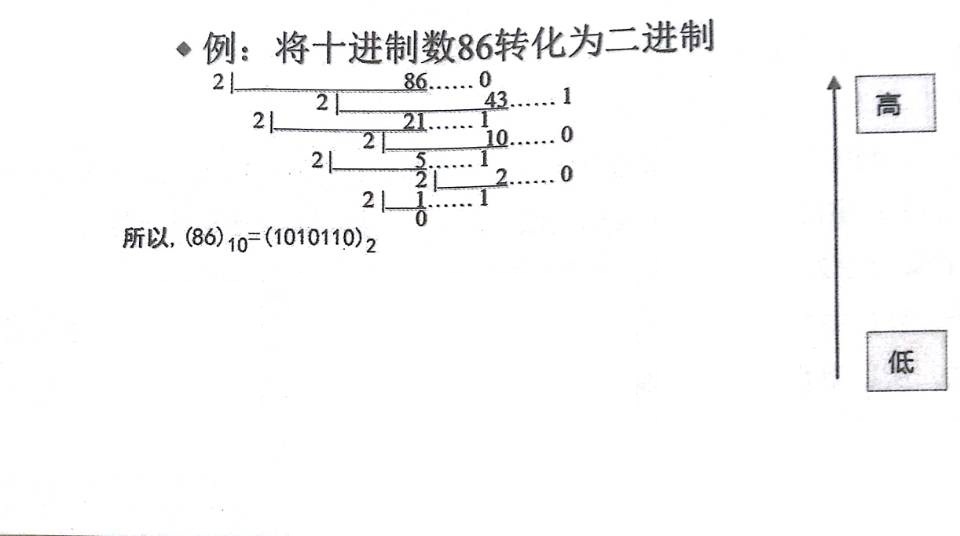
1.2 Dezimalzahl in die Binärzahl umsetzen
Durch 2 Rest bekommen,bis der Quotient 0 ist,liest man von unten nach oben
Integral:
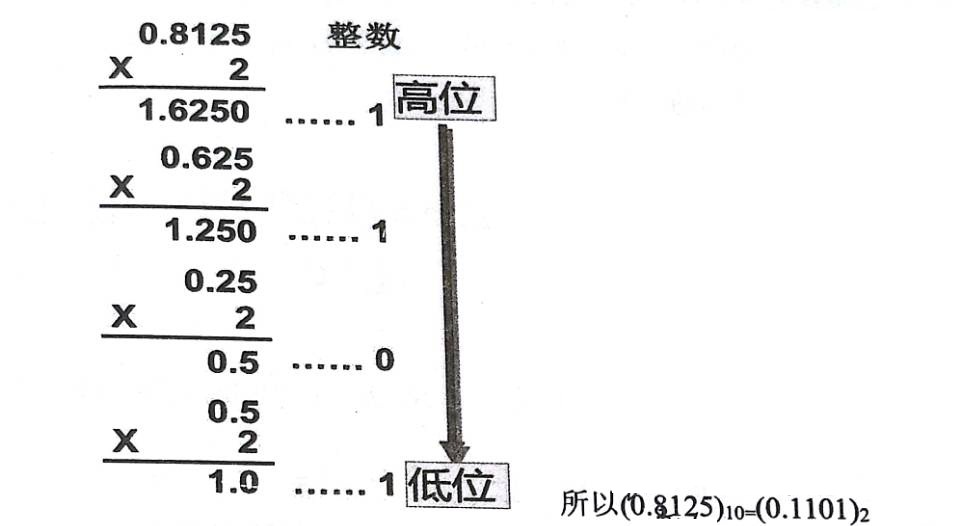
Dezimale:Mal 2 Integral bekommen,bis Dezimaleteil 0 ist,liest man von oben nach unten
1.3 Binärzahl in die Oktalzahl umsetzen
Drei Binärzahl schliessen ein Oktalzahl zusammen.
Integralteil:von Rechts nach Links,drei Zahl in eine Gruppe,falls Zahl nicht genug,fugen 0 hinzu.
Dezimaleteil:von Links nach Rechts,drei Zahl in eine Gruppe,falls Zahl nicht genug,fugen 0 hinzu.

1.4 Oktalzahl in die Binärzahl umsetzen
Eine Oktalzahl teilt in drei Binärzahl ein

1.5 Ursprünglicher Code
Man erklart Zeichen mit Hohe Position.

1.6 Inverse Code
Der inverse Code der positve Zahl ist gleich wie Ursprünglicher Code;Zeichenposition der negative Zahl ist 1,berechnen die restlich Position umgekehrt(1->0 order 0->1)

1.7 Ergänzungscode
Der Ergänzungscode der positve Zahl ist gleich wie ursprünglicher Code und inverse Code;Zeichenposition der negative Zahl ist 1;Der inverse Code plus 1,dann erlangen wir Ergänzungscode.


Chapter 1: A Tour of Computer Systems
A computer system consists of hardware and systems software that work together to run application programs.
We begin our study of systems by tracing the lifetime of the hello program, from the time it is created by a programmer, until it runs on a system, prints its simple message, and terminates.
#include <stdio.h>
int main(void)
{
printf("hello, world\n");
}
1.1 Information Is Bits + Context
The hello.c program is stored in a file as a sequence of bytes, we shows the ASCII representation of the hello.c program:

Files such as hello.c that consist exclusively of ASCII characters are known as text files.All other files are known as binary files.
The representation of hello.c illustrates a fundamental idea: All information in a system--including disk files, programs stored in memory, user data stored in memory, and data transferred across a network--is represented as a bunch of bits.The only thing that distinguishes different data objects is the context in which we view them.
1.2 Programs Are Translated by Other Programs into Different Forms
in order to run hello.c on the system, the individual C statements must be translated by other programs into a sequence of low-level machine-language instructions.These instructions are then packaged in a form called an executable object program and stored as a binary disk file.Object programs are also referred to as executable object files.
we run hello.c in unix system:
lgtdeMacBook-Pro:~ lgt$ gcc -o hello hello.c
lgtdeMacBook-Pro:~ lgt$ ls hello*
hello hello.c
lgtdeMacBook-Pro:~ lgt$ ./hello
hello, world
Preprocessing phase:The preprocessor(cpp) modifies the original C program according to directives that begin with the # character.For example, the #include<stdio.h> command in line 1 of hello.c tells the preprocessor to read the contents of the system header file stdio.h and insert it directly into the program text. The result is another C program, typically with the .i suffix.
Compilation phase:The compiler(cc1) translates the text file hello.i into the text file hello.s, which contains an assembly-language program.Each statement in an assembly-language program exactly describes one low-level machine-language instruction in a standard text form.Assembly language is useful because it provides a common output language for different compilers for different high-level languages.
Assembly phase: The assembler(as) translates hello.s into machine-language instructions, packages then in a form known as a relocatable object program, and stores the result in the object file hello.o.The hello.o file is a binary file whose bytes encode machine language instructions rather than characters.
Linking phase:The printf function resides in a separate precompiled object file called print.o, which must somehow be merged with our hello.o program. The linker(ld) handles this merging.The result is the hello file, which is an executable object file(or simply executable) that is ready to be loaded into memory and executed by the system.
1.3 It Pays to Understand How Compilation Systems Work
how compilation system work: Optimizing program performance, Understanding link-time errors and Avoiding security holes.
1.4 Processors Read and Interpret Instructions Stored in Memory
1.4.1 Hardware Organization of a System
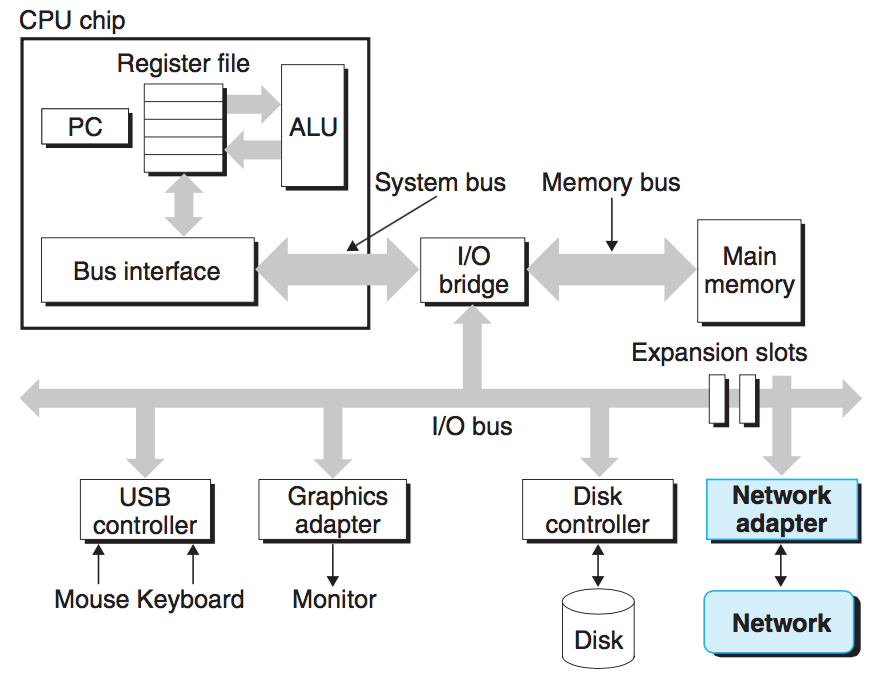
To understand what happens to our hello program when we run it, we need to understand the hardware organization of a typical system:
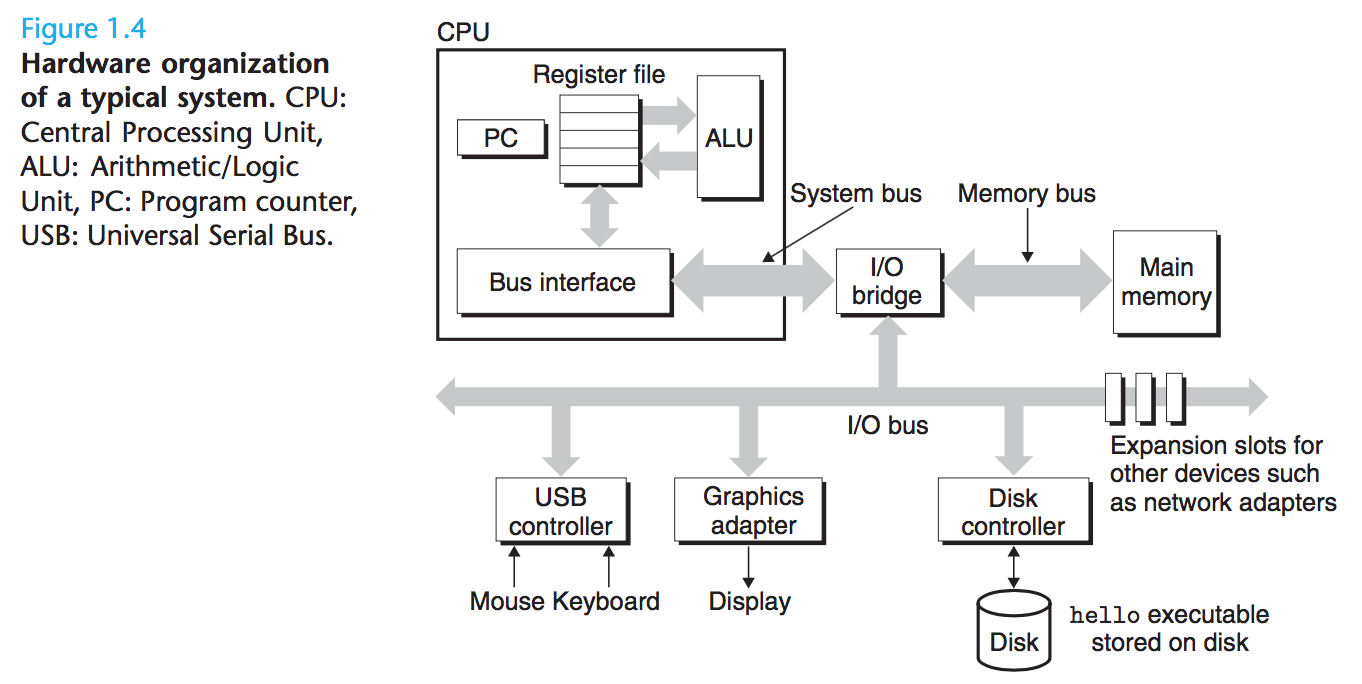
Buses
Running throughout the system is a collection of electrical conduits called buses that carry bytes of information back and forth between the components. Buses are typically designed to transfer fixed-sized chunks of bytes known as words.The number of bytes in a word(the word size) is a fundamental system parameter that varies across systems.
I/O Devices
Input/output(I/O) devices are the system''s connection to the external world.
Each I/O device is connected to the I/O bus by either a controller or an adapter. Controllers are chip sets in the device itself or on the system''s main printed circuit board(often called the mother board). An adapter is a card that plugs into a slot on the motherboard. Regardless, the purpose of each is to transfer information back and forth between the I/O bus and an I/O device.
Main Memory
The main memory is a temporary storage device that holds both a program and the data it manipulates while the processor is executing the program. Physically, main memory consists of a collection of dynamic random access memory(DRAM) chips. Logically, memory is organized as a linear array of bytes, each with its own unique address(array index) starting at zero. In general, each of the machine instructions that constitute a program can consist of a variable number of bytes. The sizes of data items that correspond to C program variables vary according to type.
Processor
The central processing unit(CPU) or simply processor, is the engine that interprets(or executes) instructions stored in main memory.At its core is a word-sized storage device(or register) called the program counter(PC). At any point in time, the PC points at (contains the address of) some machine-language instruction in main memory.
From the time that power is applied to the system, until the time that the power is shut off, a processor repeatedly executes the instruction pointed at by the program counter and updates the program counter to point to the next instruction. A processor appears to operate according to a very simple instruction execution model, defined by its instruction set architecture. In this model, instructions execute in strict sequence, and executing a single instruction involves performing a series of steps. The processor reads the instruction from memory pointed at by the program counter(PC), interprets the bits in the instruction, performs some simple operation dictated by the instruction, and then updates the PC to point to the next instruction, which may or may not be contiguous in memory to the instruction that was just executed.
There are only a few of these simple operations, and they revolve around main memory, the register file, and the arithmetic/logic unit(ALU). The register file is a small storage device that consists of a collection of word-sized registers, each with its own unique name. The ALU computes new data and address values. Here has some example:
Load: Copy a byte or a word from main memory into a register, overwriting the previous contents of the register.
Store: Copy a byte or a word from a register to a location in main memory, overwriting the previous contents of that location.
Operate: Copy the contents of two registers to the ALU, perform an arithmetic operation on the two words, and store the result in a register, overwriting the previous contents of that register.
Jump: Extract a word from the instruction itself and copy that word into the program counter(PC), overwriting the previous value of the PC.
1.4.2 Running the hello Program
When we type the characters "./hello" at the keyboard, the shell program reads each one into a register, and then stores it in memory:
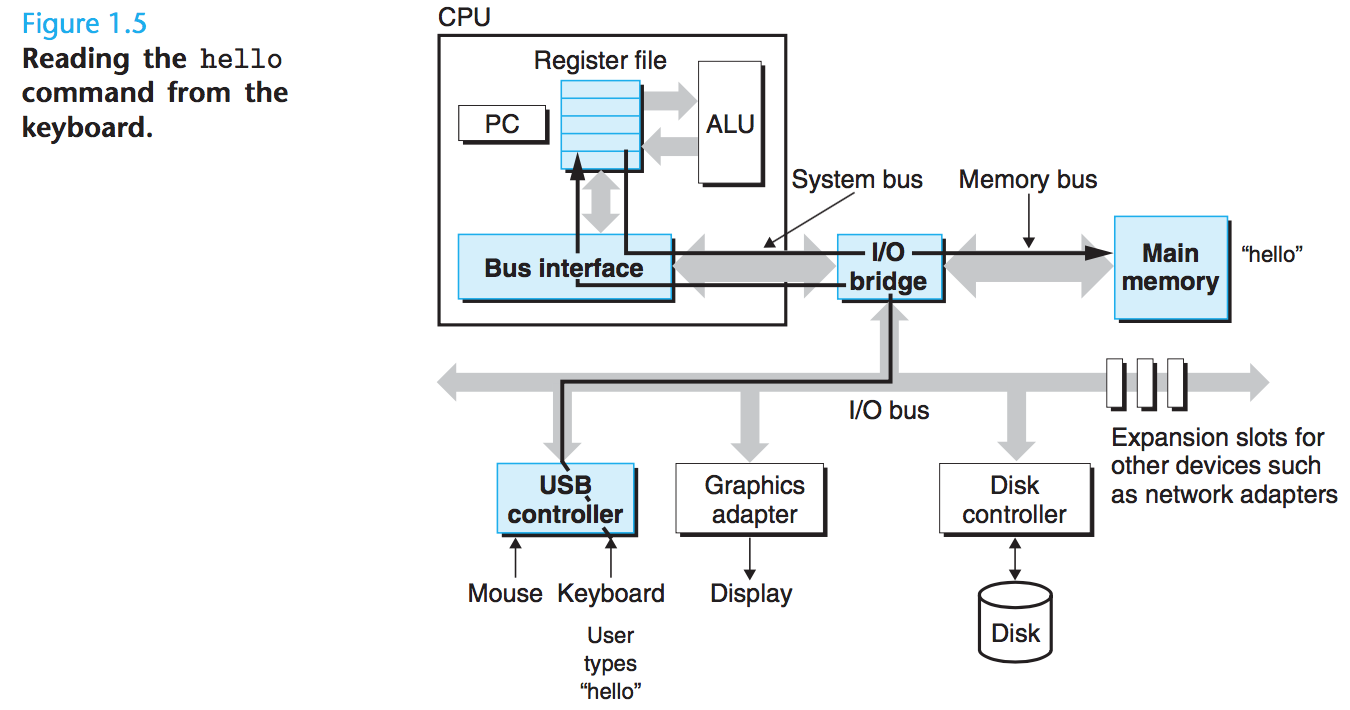
When we hit the enter, the shell then loads the executable hello file by executing a sequence of instructions that copies the code and data in the hello object file from disk to main memory. The data include the string of characters "hello, world\n" that will eventually be printed out:

Once the code and data in the hello object file are loaded into memory, the processor begins executing the machine-language instructions in the hello program''s main routine.

1.5 Caches Matter
We know that processor is faster than main memory, and main memory is faster than disk when moving information from one place to another.
To deal with the processor-memory gap, system designers include smaller faster storage devices called cache memories(or simply caches) that serve as temporary staging areas for information that the processor is likely to need in the near future.

An L1 cache on the processor chip holds tens of thousands of bytes and can be accessed nearly as fast as the register file. A larger L2 cache with hundreds of thousands to millions of bytes is connected to the processor by a special bus. It might take 5 times longer for the process to access the L2 cache than the L1 cache, but this is still faster than accessing the main memory. The L1 and L2 caches are implemented with a hardware technology known as static random access memory(SRAM).
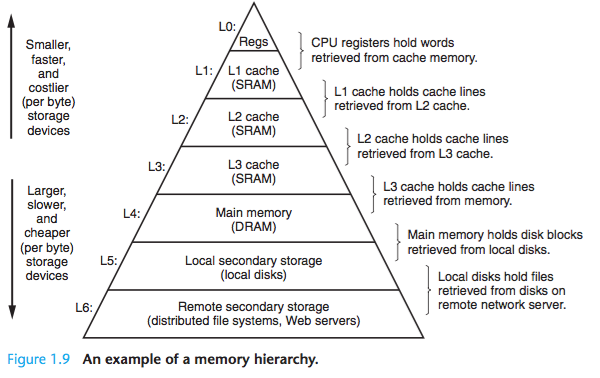
1.6 Storage Devices Form a Hierarchy
memory hierarchy:
1.7 The Operating System Manages the Hardware
Back to our hello example. When the shell loaded and ran the hello program, and when the hello program printed its message, neither program accessed the keyboard, display, disk, or main memory directly. Rather, they relied on the services provided by the operating system. We can think of the operating system as a layer of software interposed between the application program and the hardware. All attempts by an application program to manipulate the hardware must go through the operating system.
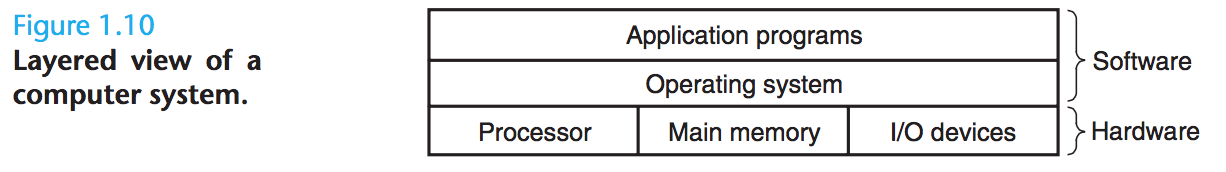
The operating system has two primary purposes:(1) to protect the hardware from misuse by runaway applications, and (2) to provide applications with simple and uniform mechanisms for manipulating complicated and often wildly different low-level hardware devices.

files are abstractions for I/O devices, virtual memory is an abstraction for both the main memory and disk I/O devices, and processes are abstractions for the processor, main memory, and I/O devices.
1.7.1 Processes
A process is the operating system''s abstraction for a running program.
The operating system keeps track of all the state information that the process needs in order to run. This state, which is known as the context, includes information such as the current values of the PC, the register file, and the contents of main memory. At any point in time, a uniprocessor system can only execute the code for a single process. When the operating system decides to transfer control from the current process to some new process, it performs a context switch by saving the context of the current process, restoring the context of the new process, and then passing control to the new process.
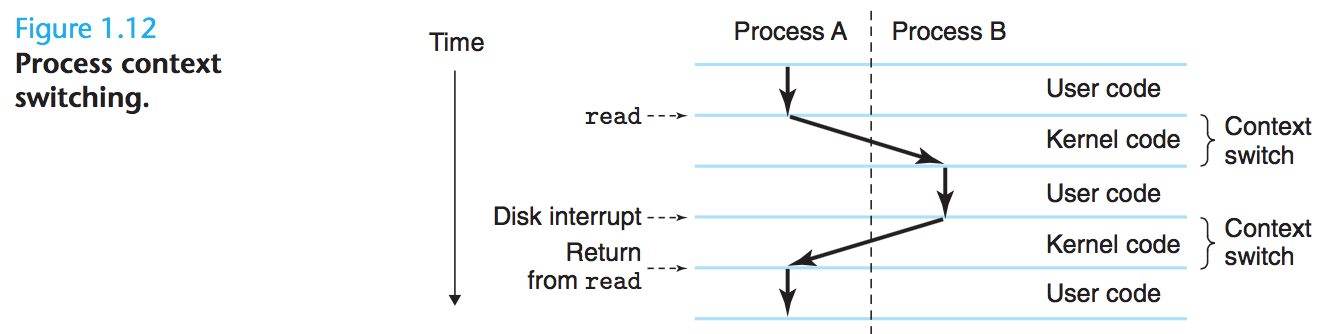
1.7.2 Threads
threads running in the context of the process and sharing the same code and global data.
1.7.3 Virtual Memory
Virtual memory is an abstraction that provides each process with the illusion that it has exclusive use of the main memory. Each process has the same uniform view of memory, which is known as its virtual address space.
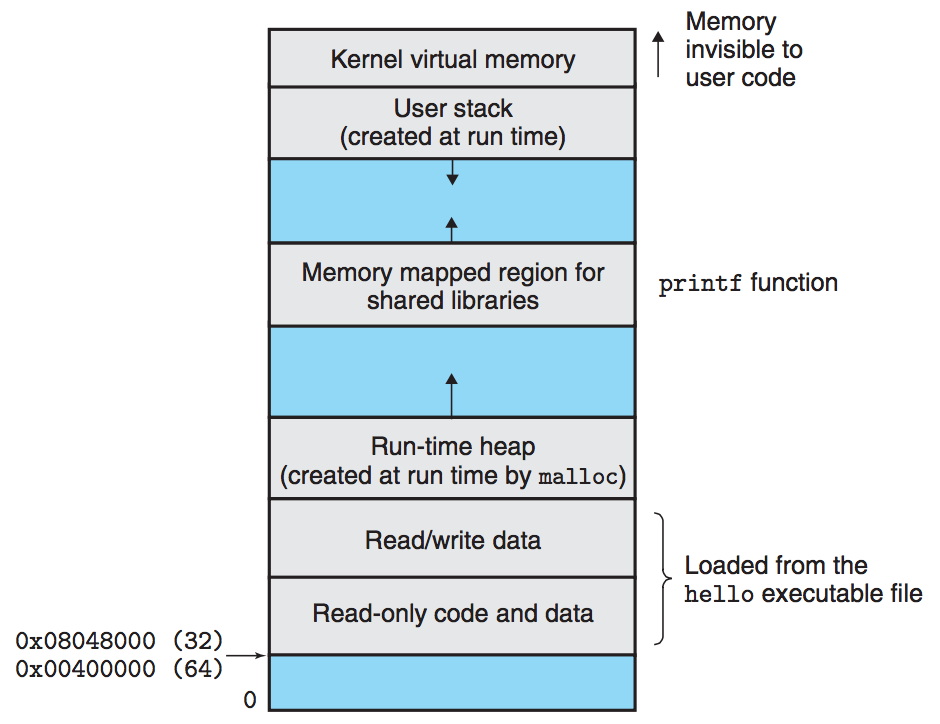
1.7.4 Files
A file is a sequence of bytes.
1.8 Systems Communicate with Other Systems Using Networks
The network can be viewed as just another I/O device. With the advent of global networks such as the Internet, copying information from one machine to another has become one of the most important uses of computer systems:
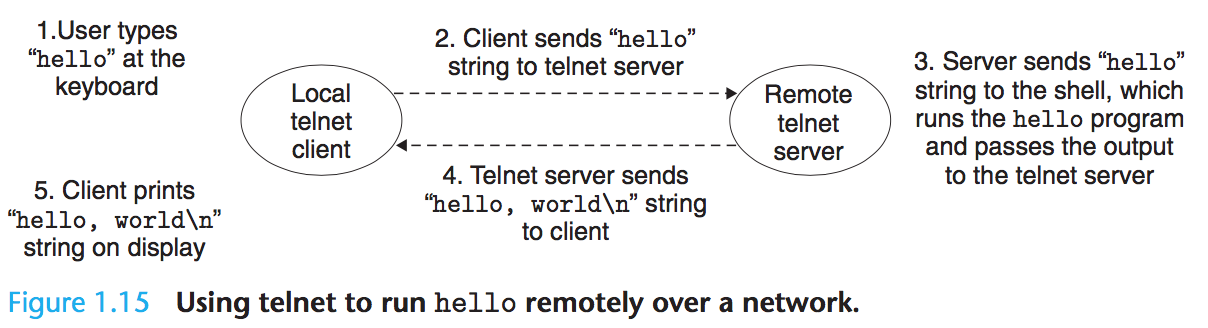
Returning to our hello example, we could use the familiar telnet application to run hello on a remote machine:
1.9 Important Themes
1.9.1 Concurrency and Parallelism
we want computer to do more, and we want them to run faster. Both of these factors improve when the processor does more things at once. We use the term concurrency to refer to the general concept of a system with multiple, simultaneous activities, and the term parallelism to refer to the use of concurrency to make a system run faster.Parallelism can be exploited at multiple levels of abstraction in a computer system.
Thread-Level Concurrency
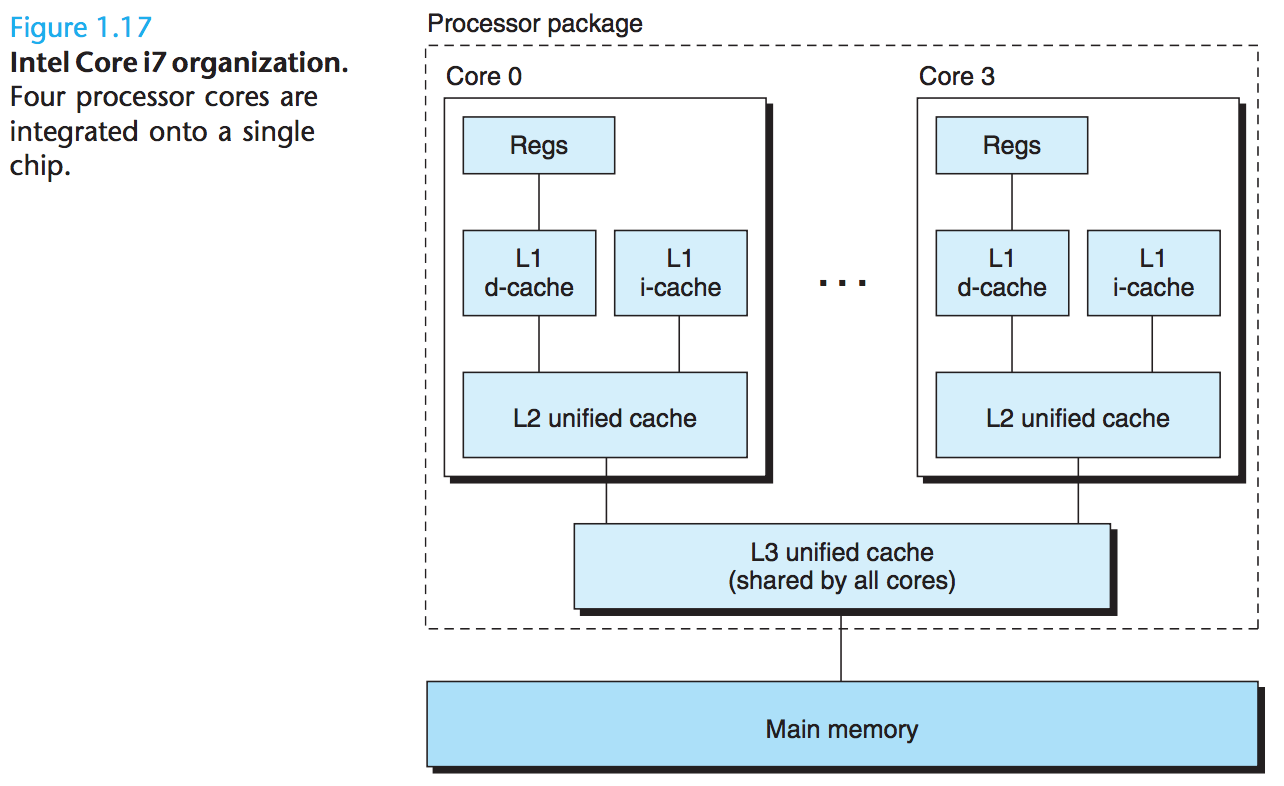
We use multi-core processors and hyper threading to make a system to consist of multiple processors.
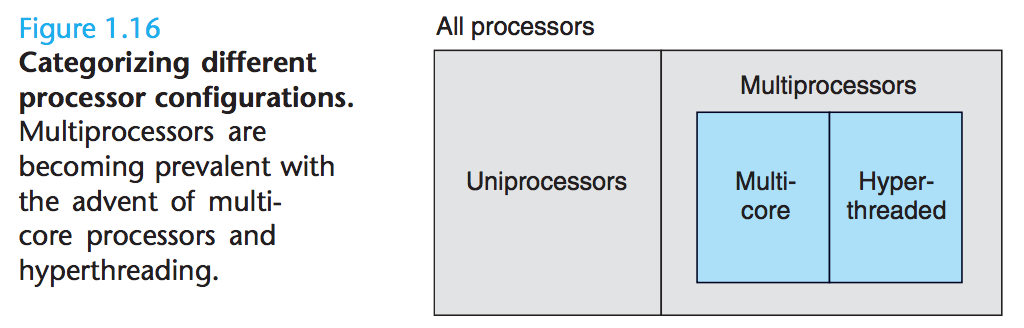
Multi-core processors have several CPUs integrated onto a single integrated-circuit chip:
Hyperthreading, sometimes called simultaneous multi-threading, is a technique that allows a single CPU to execute multiple flows of control.It involves having multiple copies of some of the CPU hardware, such as program counters and register files, while having only single copies of other parts of the hardware, such as the units that perform floating-point arithmetic.
今天关于CE235 Computer Security的讲解已经结束,谢谢您的阅读,如果想了解更多关于3D Computer Grapihcs Using OpenGL - 18 相机移动、A Self-Organized Computer Virus Demo in C、An Introduction to Computer Thinking、Chapter 1: A Tour of Computer Systems的相关知识,请在本站搜索。
本文标签:





