本文将为您提供关于ACCESS_COARSE_LOCATION权限在Android上提供了单元格塔精度的详细介绍,我们还将为您解释access-control-allow-orign指定的相关知识,同
本文将为您提供关于ACCESS_COARSE_LOCATION权限在Android上提供了单元格塔精度的详细介绍,我们还将为您解释access-control-allow-orign 指定的相关知识,同时,我们还将为您提供关于Accessing private Application Load Balancers and EC2 instances through AWS Global Accelerator、ACCESS_COARSE_LOCATION在Android 6上不起作用、ACCESS_FINE_LOCATION权限是否包括ACCESS_COARSE_LOCATION权限、ACCESS_MEDIA_LOCATION权限请求未显示提示的实用信息。
本文目录一览:- ACCESS_COARSE_LOCATION权限在Android上提供了单元格塔精度(access-control-allow-orign 指定)
- Accessing private Application Load Balancers and EC2 instances through AWS Global Accelerator
- ACCESS_COARSE_LOCATION在Android 6上不起作用
- ACCESS_FINE_LOCATION权限是否包括ACCESS_COARSE_LOCATION权限
- ACCESS_MEDIA_LOCATION权限请求未显示提示

ACCESS_COARSE_LOCATION权限在Android上提供了单元格塔精度(access-control-allow-orign 指定)
我正在使用FusedLocationApi中的requestLocationUpdates()函数进行一些测试.我使用的是PRIORITY_BALANCED_POWER_ACCURACY.城市街区精度对我来说很好.
当我申请ACCESS_FINE_LOCATION许可时,我得到了100米的精度,这对于GPS关闭是很好的.由于我不需要GPS精度但是城市块精度,我想只请求ACCESS_COARSE_LOCATION权限.但是,当我请求ACCESS_COARSE_LOCATION权限时,我得到2公里的精度.看来该设备不再使用Wifi权限,只使用单元塔精度.
如何通过ACCESS_COARSE_LOCATION许可获得更好的精度?
注意:我的测试设备上禁用了GPS.
解决方法:
这是一个有趣的问题,我认为使用ACCESS_COARSE_LOCATION会使用WiFi,因为这就是文档所说的内容.
ACCESS_COARSE_LOCATION的文档说明:
Allows an app to access approximate location derived from network
location sources such as cell towers and Wi-Fi.
所以,我把它做了测试,结果令人惊讶.
这是我用来测试的代码:
public class MainActivity extends Activity implements
Googleapiclient.ConnectionCallbacks, Googleapiclient.OnConnectionFailedListener, LocationListener {
LocationRequest mLocationRequest;
Googleapiclient mGoogleapiclient;
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_main);
buildGoogleapiclient();
mGoogleapiclient.connect();
}
@Override
protected void onPause(){
super.onPause();
if (mGoogleapiclient != null) {
LocationServices.FusedLocationApi.removeLocationUpdates(mGoogleapiclient, this);
}
}
protected synchronized void buildGoogleapiclient() {
Toast.makeText(this,"buildGoogleapiclient",Toast.LENGTH_SHORT).show();
mGoogleapiclient = new Googleapiclient.Builder(this)
.addConnectionCallbacks(this)
.addOnConnectionFailedListener(this)
.addApi(LocationServices.API)
.build();
}
@Override
public void onConnected(Bundle bundle) {
Toast.makeText(this,"onConnected",Toast.LENGTH_SHORT).show();
mLocationRequest = new LocationRequest();
mLocationRequest.setInterval(10);
mLocationRequest.setFastestInterval(10);
mLocationRequest.setPriority(LocationRequest.PRIORITY_BALANCED_POWER_ACCURACY);
//mLocationRequest.setPriority(LocationRequest.PRIORITY_LOW_POWER);
//mLocationRequest.setSmallestdisplacement(0.1F);
LocationServices.FusedLocationApi.requestLocationUpdates(mGoogleapiclient, mLocationRequest, this);
}
@Override
public void onConnectionSuspended(int i) {
Toast.makeText(this,"onConnectionSuspended",Toast.LENGTH_SHORT).show();
}
@Override
public void onConnectionFailed(ConnectionResult connectionResult) {
Toast.makeText(this,"onConnectionFailed",Toast.LENGTH_SHORT).show();
}
@Override
public void onLocationChanged(Location location) {
Log.d("locationtesting", "accuracy: " + location.getAccuracy() + " lat: " + location.getLatitude() + " lon: " + location.getLongitude());
Toast.makeText(this,"Location Changed",Toast.LENGTH_SHORT).show();
}
}
AndroidManifest.xml中:
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" />
的build.gradle:
compile 'com.google.android.gms:play-services:7.3.0'
我做的第一个测试是PRIORITY_BALANCED_POWER_ACCURACY,没有WiFi.请注意,我还禁用了“始终允许扫描”,因为它指出:
Let Google Location Service and other applications scan for Wi-Fi
networks, even when Wi-Fi is off
因此,如果启用了结果,那肯定会扭曲结果.
请注意,我还在省电模式下为所有测试设置了位置模式,因此GPS收音机一直处于关闭状态.
以下是PRIORITY_BALANCED_POWER_ACCURACY,ACCESS_COARSE_LOCATION和无WiFi的结果:
accuracy: 2000.0 lat: 37.78378378378378 lon: -122.40320943772021
因此,它表示2000米精度,这里是实际坐标的距离,绿色箭头显示我实际上在哪里:
然后,我启用了WiFi,再次运行测试,令人惊讶的是,结果完全相同!
accuracy: 2000.0 lat: 37.78378378378378 lon: -122.40320943772021
然后,我在LocationRequest中切换到LocationRequest.PRIORITY_LOW_POWER,同时在AndroidManifest.xml中保留android.permission.ACCESS_COARSE_LOCATION.
没有WiFi:
accuracy: 2000.0 lat: 37.78378378378378 lon: -122.40320943772021
有WiFi:
accuracy: 2000.0 lat: 37.78378378378378 lon: -122.40320943772021
结果再次完全相同!
使用PRIORITY_LOW_POWER与使用PRIORITY_BALANCED_POWER_ACCURACY具有相同的结果,因为WiFi状态似乎对坐标的准确性没有任何影响.
然后,为了覆盖所有基础,我改回了LocationRequest.PRIORITY_BALANCED_POWER_ACCURACY,并将AndroidManifest.xml切换到ACCESS_FINE_LOCATION:
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" />
首次测试,没有WiFi:
accuracy: 826.0 lat: 37.7825458 lon: -122.3948752
所以,它说准确度为826米,这是它在地图上的接近程度:
然后,我启动了WiFi,结果如下:
accuracy: 18.847 lat: 37.779679 lon: -122.3930918
正如您在地图上看到的那样,它实际上是正确的:
似乎在Java代码中你在LocationRequest中使用的更少,以及你在AndroidManifest.xml中使用的权限更多,因为这里的结果清楚地表明,当使用ACCESS_FINE_LOCATION时,打开或关闭WiFi无线电是一个巨大的精度差异,一般来说也更准确.
看起来好像文档有点突然出现,并且在使用android.permission.ACCESS_COARSE_LOCATION时,当您的应用程序是唯一一个提出位置请求时,打开或关闭WiFi无线电并没有什么不同.
文档说明的另一件事是使用PRIORITY_BALANCED_POWER_ACCURACY会让您的应用程序“捎带”到其他应用程序发出的位置请求.
从文档:
They will only be assigned power blame for the interval set by
setInterval(long), but can still receive locations triggered by other
applications at a rate up to setFastestInterval(long).
因此,如果用户打开Google地图,根据文档,您的应用可以在此时获得更准确的位置.这是使用新的Fused Location Provider而不是旧API的主要方面之一,因为它可以减少您的应用程序的电池消耗量,而无需您做太多工作.
编辑:我对此功能进行了测试,以了解使用ACCESS_COARSE_LOCATION时会发生什么.
首次测试:ACCESS_COARSE_LOCATION,PRIORITY_BALANCED_POWER_ACCURACY和WiFi on:
accuracy: 2000.0 lat: 37.78378378378378 lon: -122.38041129850662
这让我在水中,离我现在的位置很远.
然后,我退出了测试应用程序,启动了Google地图,它确切地定位了我,然后重新启动了测试应用程序.
测试应用程序无法从Google地图上捎带到该位置,结果与以前完全相同!
accuracy: 2000.0 lat: 37.78378378378378 lon: -122.38041129850662
我重新测试了几次,只是为了确定,但它看起来真的好像使用ACCESS_COARSE_LOCATION也会禁用应用程序“捎带”到其他应用程序获取的位置的能力.
看起来在AndroidManifest.xml中使用ACCESS_COARSE_LOCATION会在获取精确位置数据方面严重削弱应用程序.
总而言之,您唯一能做的就是磨练适合您和您的应用程序的最佳设置组合,并希望此测试的结果可以帮助您做出决定.

Accessing private Application Load Balancers and EC2 instances through AWS Global Accelerator

https://amazonaws-china.com/blogs/networking-and-content-delivery/accessing-private-application-load-balancers-and-instances-through-aws-global-accelerator/
Many Content Distribution Networks (CDNs) offer a feature to obfuscate the source origin through functionality commonly referred to as origin cloaking. Using AWS Global Accelerator with Client IP Address Preservation capability, similar functionally can be facilitated. Private Application Load Balancers (ALBs) and private EC2 instances can be accessed through Global Accelerator in a secure and simplified manner.
AWS Global Accelerator is an AWS service that improves global application availability and performance using the AWS global network. The Client IP Address Preservation feature allows you to make Global Accelerator the single internet-facing access point for your applications running in a single or multiple AWS Regions. The applications are centrally protected from distributed denial of service (DDoS) attacks through AWS Shield. You can also have greater control over how your end users reach your applications.
In this blog post, I dive into implementation best practices and walk through how to use client IP address preservation functionality in controlled environments. I also discuss ways to limit access in regulated or controlled environments where origin cloaking functionality might not be desirable.
How this functionality works in AWS Global Accelerator
The IP preservation functionally of AWS Global Accelerator is the key enabler for the origin cloaking capability. Jeff Barr’s blog post on IP preservation looks at how to implement this functionality for an Application Load Balancer (ALB).
Essentially an elastic network interface (ENI) is created within each AZ that contains the private ALB or private instances. Traffic flows from the AWS Global Accelerator elastic network interface to the backend instance or ALB. The connection is monitored and return traffic follows the same path back out over the AWS Global Accelerator elastic network interface. This traffic flow is depicted in the diagrams below for an ALB.
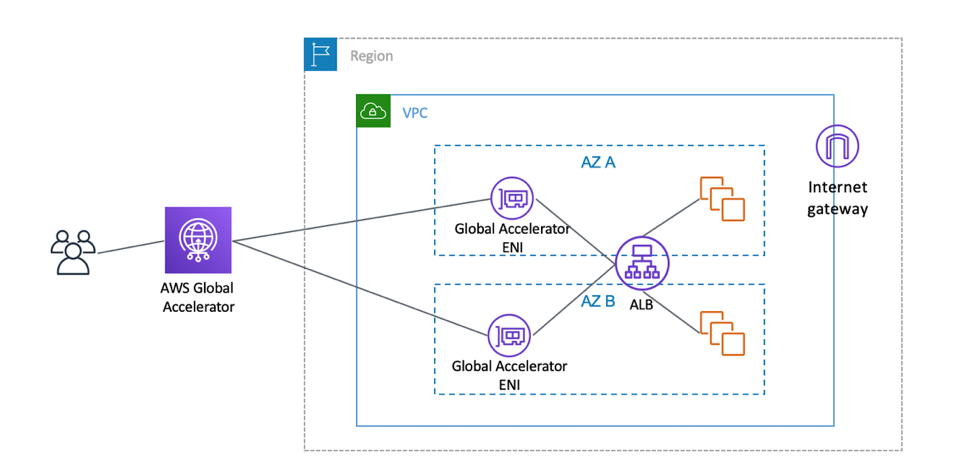
The data flow for private instances is very similar. This is shown in the diagram below.
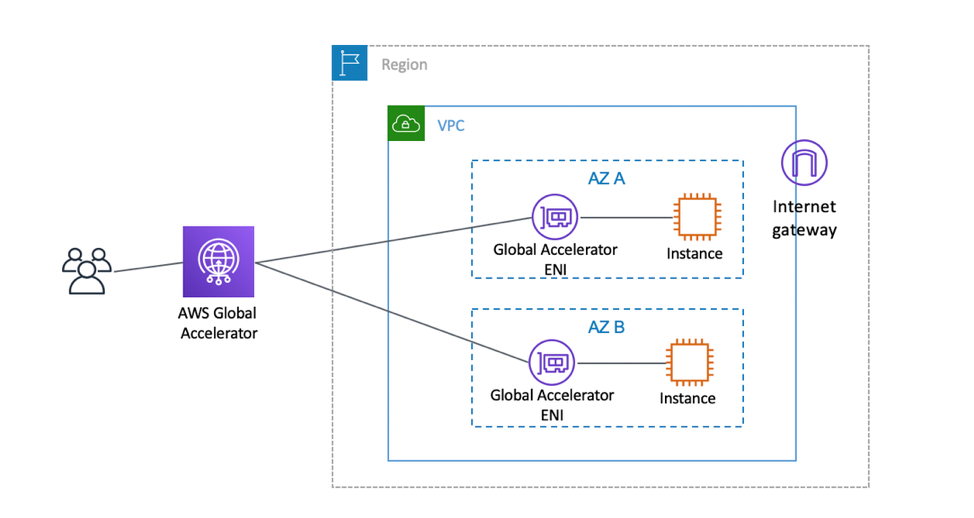
In both data flows, the instances remain private with no route out to the internet. The Global Accelerator ENIs and instances are shown in the same subnet, but can be in multiple subnets if separate route tables are required for more granular control of traffic. The next section will go deeper into how we limit access to private VPC resources.
How we limit access to private VPC resources
To avoid internet traffic from inadvertently flowing into a private subnet, we require that an internet gateway is attached to the VPC that contains resources when a client address-preserving accelerator is created. The internet gateway does not need a route in the relevant subnet route table, or any subnet route table for that matter. The subnet essentially remains private (that is to say, no route to an internet gateway). This allows organization with traditional checks for IGWs to ensure that their network security perimeter is maintained and can still be audited.
The Global Accelerator ENIs that are created only allow traffic to and from AWS Global Accelerator service. They do not allow any type of broad access to the internet. They only allow inbound connections, even when the connections are logical only (for example, for UDP traffic). Access to an ALB or instance is further still governed by security groups and network access control lists (NACLs). NACLs and security groups provide granular control to allow traffic. With security groups, specific public IP addresses can be defined as allowed. Through the use of NACLs, traffic can also be explicitly denied access to specific outbound IP addresses.
For best practices in implementing IP client preservation with Global Accelerator, you can review the documentation here.
How to disable this functionality
We provide several options for customers that want to limit and control internet connectivity to their VPCs at an organizational level. AWS Organization supports Service Control Policies (SCPs). These allow policy to be applied at an organization unit (OU) level to govern access to AWS resources.
SCPs can be created to explicitly prevent any actions that would allow access from the internet. An example of such a policy is shown here. To prevent access to Global Accelerator from restricted accounts, the following actions should be denied in an SCP: Global Accelerator:Create* and Global Accelerator:Update*.
Conclusion
IP address source preservation with Global Accelerator opens up new capabilities for deploying global applications. Origins can be cloaked behind Global Accelerator to allow a single access point that is exposed to the internet.
About the Author
 |
James Devine is a Senior Specialist Solutions Architect at AWS specializing in Networking, VMware, and Outposts. James has a BS in Computer Science from Allegheny College and an MS in Computer Science from Stevens Institute of Technology. Prior to coming to AWS James was a Senior Infrastructure Engineer at MITRE, a non-profit government contractor, where he used his skills in infrastructure to help various government organizations solve some of their toughest problems and realize the value of Cloud Computing. |

ACCESS_COARSE_LOCATION在Android 6上不起作用
这个问题已经在这里有了答案: > Android permission doesn’t work even if I have declared it 12个
我按照官方的例子来写这个程序
public class BluetoothActivity extends AppCompatActivity {
private static final long SCANNING_TIMEOUT = 5000; /* 5 seconds */
private static final int ENABLE_BT_REQUEST_ID = 1;
private BleWrapper mBleWrapper = null;
private boolean mScanning = false;
private Handler mHandler = new Handler();
private BluetoothAdapter mBluetoothAdapter;
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_bluetooth);
if (!getPackageManager().hasSystemFeature(PackageManager.FEATURE_BLUetoOTH_LE)) {
Toast.makeText(this, "no ble", Toast.LENGTH_SHORT).show();
finish();
}
final BluetoothManager bluetoothManager =
(BluetoothManager) getSystemService(Context.BLUetoOTH_SERVICE);
mBluetoothAdapter = bluetoothManager.getAdapter();
if (mBluetoothAdapter == null || !mBluetoothAdapter.isEnabled()) {
Intent enableBtIntent = new Intent(BluetoothAdapter.ACTION_REQUEST_ENABLE);
startActivityForResult(enableBtIntent, 1);
}
scanLeDevice(true);
}
private BluetoothAdapter.LeScanCallback mLeScanCallback =
new BluetoothAdapter.LeScanCallback() {
@Override
public void onLeScan(final BluetoothDevice device, int RSSi,
byte[] scanRecord) {
Log.v("ble",device.getName());
}
};
// Stops scanning after 10 seconds.
private static final long SCAN_PERIOD = 3000;
private void scanLeDevice(final boolean enable) {
if (enable) {
// Stops scanning after a pre-defined scan period.
mHandler.postDelayed(new Runnable() {
@Override
public void run() {
mScanning = false;
mBluetoothAdapter.stopLeScan(mLeScanCallback);
}
}, SCAN_PERIOD);
mScanning = true;
mBluetoothAdapter.startLeScan(mLeScanCallback);
} else {
mScanning = false;
mBluetoothAdapter.stopLeScan(mLeScanCallback);
}
}
}
这是manifests.xml中的权限
<uses-permission android:name="android.permission.BLUetoOTH" />
<uses-permission android:name="android.permission.BLUetoOTH_ADMIN" />
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" />
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" />
但是我仍然有这个例外
03-24 15:52:01.126 2223-2236/com.test W/Binder: Caught a RuntimeException from the binder stub implementation.
03-24 15:52:01.126 2223-2236/com.test W/Binder: java.lang.SecurityException: Need ACCESS_COARSE_LOCATION or ACCESS_FINE_LOCATION permission to get scan results
如何使BLE在Android 6上工作,我的设备的Android版本为6.0.1
为什么我添加了该权限,但仍然有该异常?
解决方法:
Andorid M功能在运行时请求权限.这意味着在安装您的应用程序后,它尚无使用蓝牙的权限.用户必须手动授予该权限(每次安装一次).
只需遵循官方指南-> Requesting Permissions at Run Time

ACCESS_FINE_LOCATION权限是否包括ACCESS_COARSE_LOCATION权限
正如您在指南的LocationManager API和older version中所看到的:
如果同时使用NETWORK_PROVIDER和GPS_PROVIDER,则需要 仅请求ACCESS_FINE_LOCATION权限,因为它 包括两个提供商的许可。 (允许 ACCESS_COARSE_LOCATION仅包含对NETWORK_PROVIDER的许可。)
简而言之:是的,如果您已经定义了ACCESS_FINE_LOCATION,则允许使用ACCESS_COARSE_LOCATION。

ACCESS_MEDIA_LOCATION权限请求未显示提示
如何解决ACCESS_MEDIA_LOCATION权限请求未显示提示?
我已将我的应用设置为目标AP 29,并从清单中删除了requestLegacyExternalStorage=true。
现在,我正在检查用户是否具有此权限,如果结果被拒绝,我将请求权限。
我的问题是,权限请求正在返回Granted,而没有显示提示...我知道流程是有效的,因为我能够在被授予后从图片中读取GPS位置。
我看到权限状态= Denied,并且在我明确请求此权限后,它会返回Granted,而无需任何用户交互。
一切看起来都不错,但我对没有看到提示感到困惑... 这是预期的吗?我看到此许可被视为“危险”,因此我希望得到提示。我正在Android 10设备上进行测试。
由于该项目是Xamarin,并且权限逻辑是通过第三方库处理的,所以我没有显示任何代码,不要认为我的代码会有所帮助,因为该组件隐藏了请求权限的平台逻辑。 / p>
解决方法
暂无找到可以解决该程序问题的有效方法,小编努力寻找整理中!
如果你已经找到好的解决方法,欢迎将解决方案带上本链接一起发送给小编。
小编邮箱:dio#foxmail.com (将#修改为@)
我们今天的关于ACCESS_COARSE_LOCATION权限在Android上提供了单元格塔精度和access-control-allow-orign 指定的分享就到这里,谢谢您的阅读,如果想了解更多关于Accessing private Application Load Balancers and EC2 instances through AWS Global Accelerator、ACCESS_COARSE_LOCATION在Android 6上不起作用、ACCESS_FINE_LOCATION权限是否包括ACCESS_COARSE_LOCATION权限、ACCESS_MEDIA_LOCATION权限请求未显示提示的相关信息,可以在本站进行搜索。
本文标签:





