对于想了解IntroductionofJSONProcessingandbindinginJavaEE的读者,本文将是一篇不可错过的文章,并且为您提供关于AsimpleintroductiontoTh
对于想了解Introduction of JSON Processing and binding in JavaEE的读者,本文将是一篇不可错过的文章,并且为您提供关于A simple introduction to Three kinds of Delegation of Kerberos、Allocation Profiling in Java Mission Control、An Introduction to Protocol Oriented Programming in Swift、API Guides -> Introduction -> Introduction to Android的有价值信息。
本文目录一览:- Introduction of JSON Processing and binding in JavaEE
- A simple introduction to Three kinds of Delegation of Kerberos
- Allocation Profiling in Java Mission Control
- An Introduction to Protocol Oriented Programming in Swift
- API Guides -> Introduction -> Introduction to Android

Introduction of JSON Processing and binding in JavaEE
ava EE提供了一个API来解析, 使用对象模型转换和查询JSON数据流 模型中描述生成和解析 JSON数据。
JSON处理包含以下的Java API 包:
①javax.json包包含一个阅读器接口,一个作家 接口,对象模型,模型构建器界面和实用性 为JSON元素类和Java类型。 这个包还包括 几类,实现其他json相关标准:JSON指针,JSON补丁,JSON合并补丁。 这些标准是用于检索、转换或操作值 在一个对象模型
②javax.json.stream和一个包包含一个解析器接口 发电机界面流模型。
③javax.json.spi包包含一个服务提供程序接口(SPI) 插入实现JSON处理对象。 这个包 包含了JsonProvider类,它包含一个服务的方法 提供者实现。

A simple introduction to Three kinds of Delegation of Kerberos
1.What is Delegation?
Just like the name. Delegation is that a server pretend to behalf of a user and to authenticate with kerberos protocol.There are three kinds of delegations.
| Kinds of Delegations | Limitions | Protocol | Note |
|---|---|---|---|
| Unconstrained Delegation | None | Just forward the TGT ticket which is able to be forwarded | None |
| Constrained Delegation | Front-End Server decide which Back-End service can receive delegation | 1.S4U2Proxy -> Forward the TGT ticket <br> 2.S4U2Self -> Receive information of NTLM Authentication(Username&NTLM-Hash) And use that to get TGT and send TGT and receive TGS from KDC | AD administrator account |
| Resource-Based Constrained Delegation | Back-End Services decide which Front-End service''s delegation can be received | The same as Constrained Delegation | 1.S4U2Proxy -> Can Forward TGT ticket which is not to be able to forwarded. <br> 2.You can use this cross the domain. <br> 3.Service administrator account |
2.Unconstrained Delegation
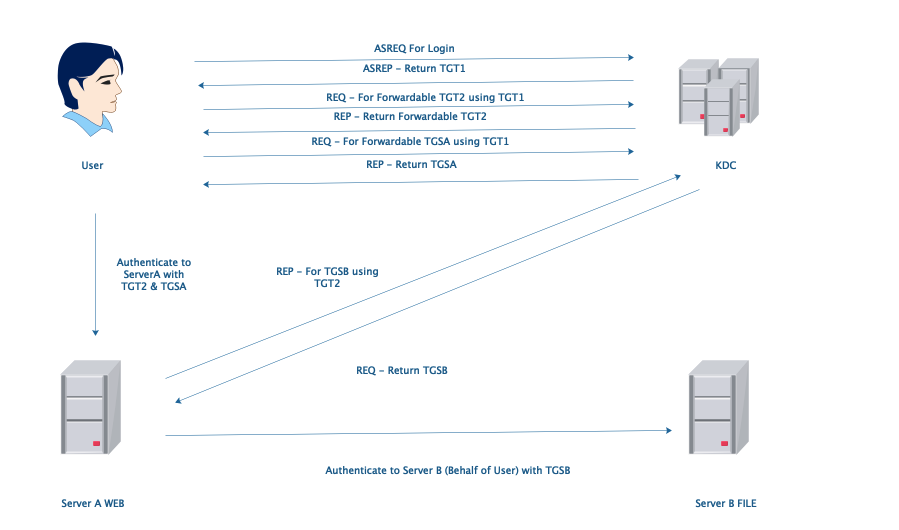
Unconstrained Delegation: ServerA can authenticate to any server in this domain behalf of user with TGT2. It is too dangerous.
3.Constrained Delegation
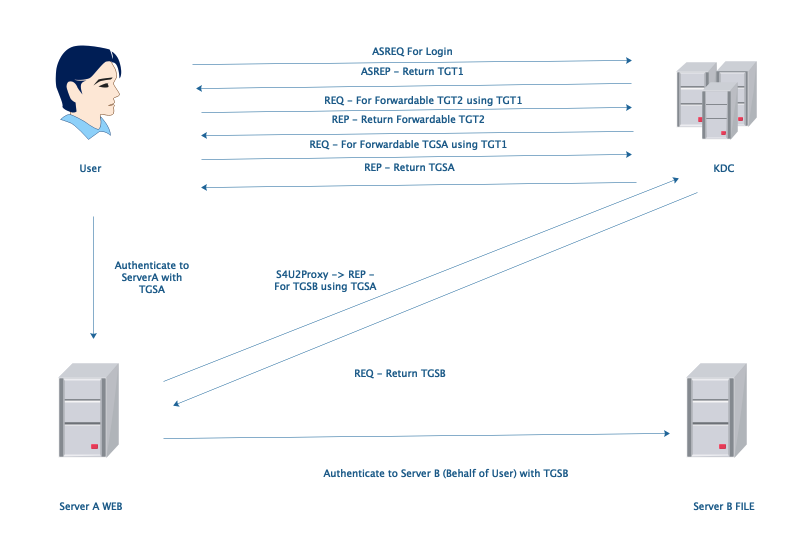
Only S4U2Proxy is what we need, if user use kerberos ticket to authenticate. Otherwise we need both S4U2Self and S4U2Proxy if user use NTLM hash to authenticate. In this condition, AD administrators can configure which service(SPNs) can receive ServerA’s delegation in ServerA''s msDC-AllowedToDelegateTo property.
4.Resource-Based Constrained Delegation
There is one important difference between Constrained Delegation and Resource-Based Constrained Delegation. In Constrained Delegation, administrators of AD can configure which service can receive ServerA''s delegation in their msDS-AllowedToActOnBehalfOfOtherIdentity properties. However, In Resource-Based Constrained Delegation, administrators of services can decide if those service will receive the ServerA''s delegation or not. And it should be configured on the computers which is running those services. Do you think Resource-Based Constrained Delegation is much more safe than Constrained Delegation? No, Resource-Based Constrained Delegation has a big problem. In this condition, S4U2Proxy can forward unforwardable TGT and KDC will return TGS back. So if we could get the TGT which is not able to forward, We also could use it to do something bad.
5. What we can do to make it a little more safe?
** We can do a lot of things to make it more safe. Plus, the first one is to configure like this.** 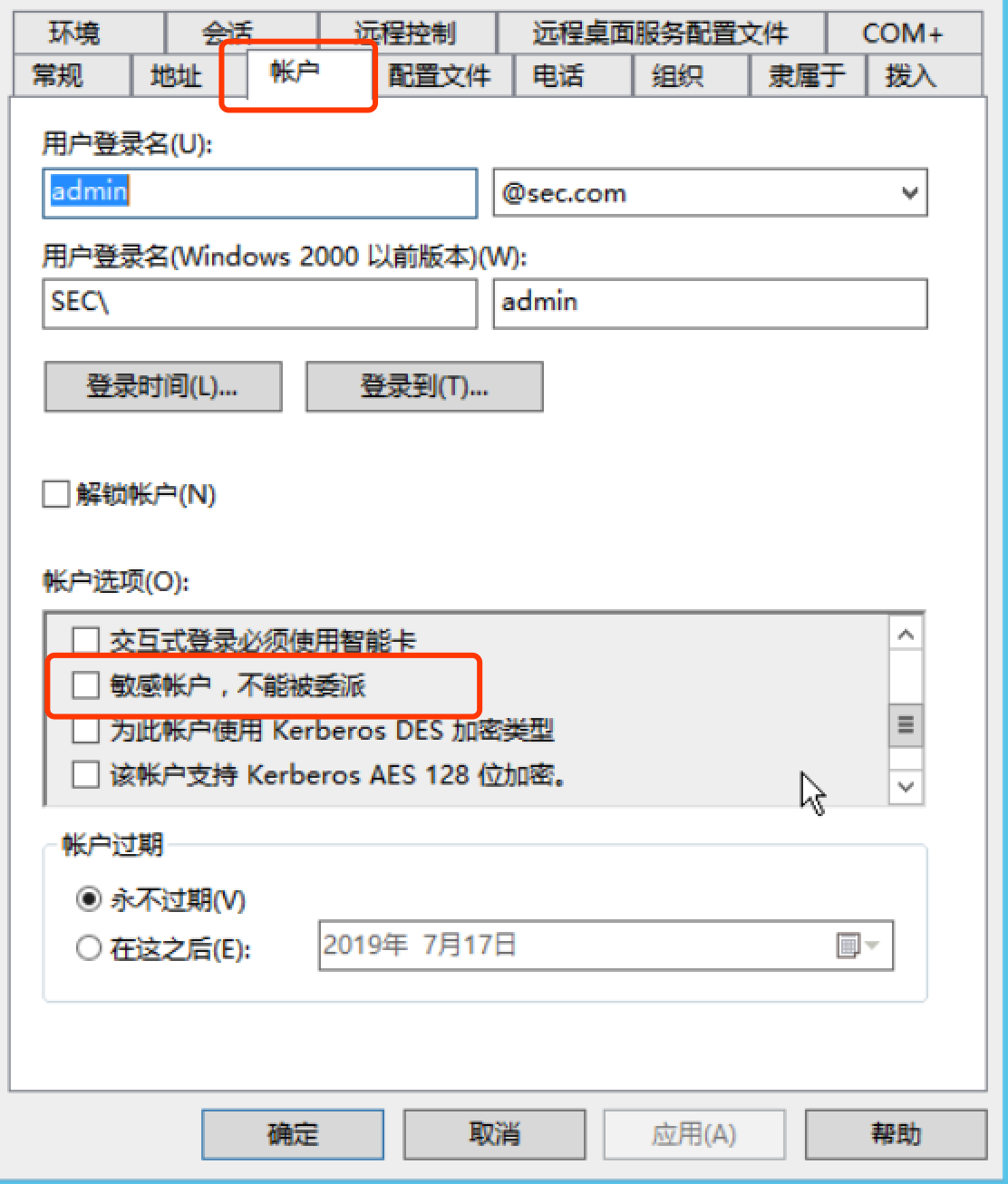

Allocation Profiling in Java Mission Control
Allocation Profiling in Java Mission Control
Thursday, September 12, 2013 - By Marcus
With the Hotspot JDK 7u40 there is a nifty new tool called Java Mission Control. Users of the nifty old tool JRockit Mission Control will recognize a lot of the features. This particular blog entry focuses on how to do allocation profiling with the Java Flight Recorder.
The JVM is a wonderful little piece of virtualization technology that gives you the illusion of an infinite heap. However that comes at a cost. Sometimes the JVM will need to find out exactly what on your heap is in use, and throw the rest away – a so called garbage collection. This is because the physical memory available to the JVM indeed is limited, and memory will have to be reclaimed and reused when it is no longer needed. In timing sensitive applications, such as trading systems and telco applications, such pauses can be quite costly. There are various tuning that can be done for the GC to make it less likely to occur. But I digress. One way to garbage collect less, is of course to allocate less.
Sometimes you may want to find out where the allocation pressure is caused by your application. There are various reasons as to why you may have reached this conclusion. The most common one is probably that the JVM is having to garbage collect more often and/or longer than you think is reasonable.
The JFR Allocation Event
In the Java Flight Recorder implementation in HotSpot 7u40 there are two allocation events that can assist in finding out where the allocations are taking place in your application: the Allocation in new TLAB and the Allocation outside TLAB events.
Just like for most events provided with the HotSpot JDK, there is of course a custom user interface for analyzing this in Mission Control, but before going there I thought we’d take a moment to discuss the actual events.
First you need to make sure they are recorded. If you bring up the default (continuous) template, you will notice that allocation profiling is off by default. Either turn it on, or use the profiling template. The reason it is off by default is that it may produce quite a lot of events, and it is a bit hard to estimate the overhead since it will vary a lot with the particular allocation behaviour of your application.
The Log tab in the Events tab group is an excellent place to look at individual events. Let’s check out what these actually contain:

They contain the allocation size of whatever was allocated, the stack trace for what caused the allocation, the class of what was allocated, and time information. In the case of the inside TLAB allocation events, they also contain the size of the TLAB.
Note that we, in the case of the (inside) TLAB allocation events, are not emitting an event for each and every location – that would be way too expensive. We are instead creating an event for the first allocation in a new TLAB. This means that we get a sampling of sorts of the thread local allocations taking place.
Also, note that in JRockit we used to have TLA events that perfectly corresponded to the allocations done in the nursery, and large object allocation events that corresponded to allocation done directly in old space. This is a little bit more complicated in HotSpot. The outside TLAB allocation events can both correspond to allocations done due to an allocation causing a young collection, and the subsequent allocation of the object in the Eden as well as the direct allocation of a humongous object directly in old space. In other words, don’t worry too much if you see the allocation of a few small objects among the outside of TLAB events. Normally these would be very few though, so in practice the distinction is probably not that important.
Using the Allocations Tab
The allocations tab actually consists of three sub tabs:
General
Allocation in new TLAB
Allocation outside TLAB
The General tab provides an overview and some statistics of the available events, such as total memory allocated for the two different event types. Depending on what your overarching goal is (e.g. tuning TLAB size, reducing overall allocation) you may use this information differently. In the example below it would seem prudent to focus on the inside TLAB allocations, as they contribute way more to the total allocation pressure.

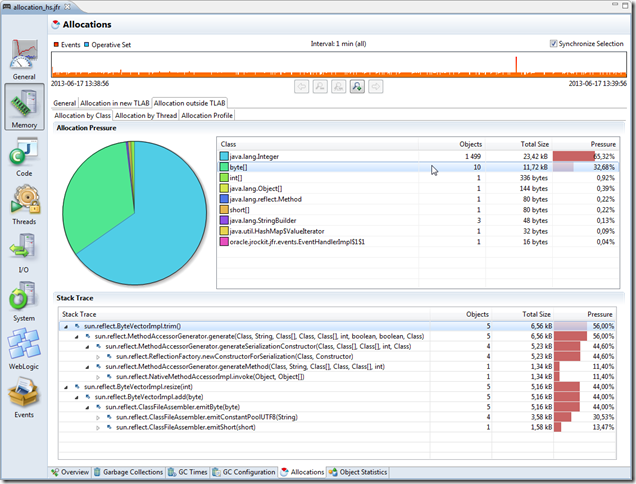
The Allocation in new TLAB tab provides three more types of visualization specific to the in new TLAB events: Allocation by Class, Allocation by Thread and Allocation Profile. The Allocation Profile is simply the aggregated stack trace tree for all of the events. In the example below it can be seen that Integer object allocations correspond to almost all the allocations in the system. Selecting the Integer class in the histogram table shows the aggregated stack traces for all the Integer allocations, and in this example all of them originate from the same place, as seen below (click in pictures to show them in full size).
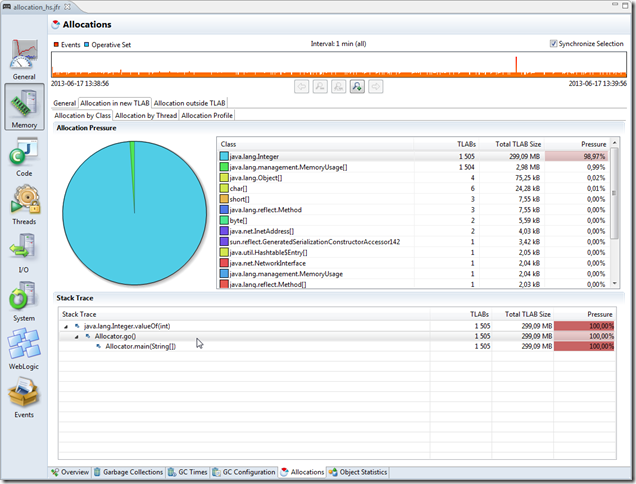
The Allocation outside TLAB tab works exactly the same way as the Allocation in new TLAB tab, only this time it is, of course, for the Allocation outside TLAB events:
Limitations
Since the Allocation in new TLAB events only represents a sample of the total thread local allocations, having only one event will say very little about the actual distribution. The more events, the more accurate the picture. Also, if the allocation behaviour vary wildly during the recording, it may be hard to establish a representative picture of the thread local allocations.
Thanks to Nikita Salnikov for requesting this blog entry!
Further reading and useful links
Related Blogs:
Java Mission Control Finally Released
Creating Flight Recordings
My JavaOne 2013 Sessions
Low Overhead Method Profiling with Mission Control
The Mission Control home page:
http://oracle.com/missioncontrol
Mission Control Base update site for Eclipse:
http://download.oracle.com/technology/products/missioncontrol/updatesites/base/5.2.0/eclipse/
Mission Control Experimental update site (Mission Control plug-ins):
http://download.oracle.com/technology/products/missioncontrol/updatesites/experimental/5.2.0/eclipse/
The Mission Control Facebook Community Page (not kidding):
http://www.facebook.com/pages/Java-Mission-Control/275169442493206

An Introduction to Protocol Oriented Programming in Swift
swift面向协议编程的根本原因在于值类型的存在;面向对象必须要有引用类型的支持;
Protocol Oriented approach was introduced to resolve some issues in programming and it also differs in varIoUs scenarios when compared to Object-Oriented programming. So let’s dive into the topic.
What is Protocol Oriented Programming?
Protocols basically serve as a blueprint like classes rather than a fully functional types for methods, properties, and other requirements. This is done to perform a piece of functionality and behaves like an interface and tells what to implement. It is a powerful feature of Swift Language. Apple tells us:
“Don’t Start with the Class, Start with the Protocol”
Why We Need POP?
When we design any software system, then we figure out the general requirements that satisfy the given system. We, even model the relationship b/w the UI elements such as buttons, view, images etc. for which we generally start with superclass and model the relationships using inheritance.
In Swift, as we have the concept of POP so, we can even start with protocols and can model the relationships as protocol implementations. In the protocol oriented approach, we model our system with a protocol, rely on the concepts like:
- Protocol Extensions
- Protocol Inheritance
- Protocol Composition
In Swift, we use structs, enums, and tuples rather than working only with classes since, Value Semantics are preferred over Reference Types.
Also, there Could be varIoUs cases where OOP is not the best solution to implement. Let’s check and figure out the drawbacks in Object-Oriented concept. We kNow that Inheritance is one of the most important concepts in OOP but, inheritance doesn’t work for value types and modern languages like Swift prohibits to support the feature of multiple inheritances due to complexities and value types is the first citizen of Swift. So, POP does a great job by providing the ability to add multiple abilities to the class, struct, and enum with protocols and extensions that supports multiple implementations while we code.
Other benefits with Protocol implementations are:
- Swift checks whether the requirements of the protocol are full-filled or not for the classes we are implementing at compile-time, so, this helps us to find out if there were any issues or bugs in code even before we ran our program.
- Also, protocols bring more abstraction mechanism than classes do in Swift.
- We’re not restricted to only use classes since any type, including value types, can implement a protocol.
- A type can implement multiple protocols.
- We can create as many protocols as we need.
Before I talk about POP in detail and how to use and implement it, we must understand the basics right, so let us focus on Swift Types first. Here is the diagrammatic representation of Swift Types that we have.
Well, here I am interested in the behavior of Classes and Structure, one belongs to the reference type and other to value type and observe how objects behave through an example.
And, this is really important to understand and why is it so? If you have a very complex hierarchy and you set something in one part of the code, it should not have any wrong consequences in the other part. So, the lesson is:
- Classes use reference i.e if you set something to other it is not a copy instead it is a reference.
- Whereas, in value type such as structures, passes things as a copy, not as a reference.
Conclusion
Apple, always recommends going with the value type while we program in Swift. Structures are preferable when we have a small copy of data and it is much safer than having multiple references to the same objects in our code. The concept becomes more important when we talk about variable and passing their value. In Swift, we work in a multi-threaded environment and if we have copies of variable then, we don’t need to worry about them in the other place where value may get change. So, using structure is advised by Apple and Protocol-Oriented Programming serves better abstraction with structures.
Using Protocols and it’s extensions features, we can really ignore/avoid for making a huge superclass and then inheriting functionality from there. So, Hope it is Now clear to you what is POP and why Apple use this.
Note: This does not mean that we don’t use Class, there are some situations where classes are the only option left for our implementation.
In the other part of this article, we will see how to implement and use protocols, protocol extensions, Generics with the protocol.
https://www.technotification.com/2018/08/protocol-oriented-programming-swift.html

API Guides -> Introduction -> Introduction to Android
介绍 Android
在基于 Java 语言环境的移动端,Android 提供了一个非常丰富的框架来让你开发出创新的应用和游戏。文档左侧的导航,详细的列出了如何使用各种 APIs 来构建 app
如果你是一个开发新手,弄懂 Android 应用框架的基本概念是非常重要的。
app 提供了多样的切入点
Android apps 由多个独立的可被调用的组件构建而成。例如,一个独立的 Activity 提供一个单独的页面在用户屏幕上,而一个 service 则在后台无关联的执行任务。
你可以使用 Intent 从一个组件启动另一个组件,你甚至可以启动一个其他 app 中的组件,例如一个 activity 启动一个地图 app 展示一个街道。这种多切入点模式,使得一个 app 可以被其他 app 用一种用户默认的动作启动。(不确定:This model provides multiple entry points for a single app and allows any app to behave as a user’s “default” for an action that other apps may invoke.)
更多
- app 基本原理
- Intents 和 Intent Filters
- Activities
Apps 适配不同的设备
Android 提供一个适配性的框架,为不同的设备配置唯一的资源。例如,你可以为不同的屏幕尺寸设计不同的 xml layout 文件,而由系统根据当前设备的尺寸来选择使用不同的 layout。
- 设备兼容性
- 资源概述
- 用户界面概述
关于Introduction of JSON Processing and binding in JavaEE的问题就给大家分享到这里,感谢你花时间阅读本站内容,更多关于A simple introduction to Three kinds of Delegation of Kerberos、Allocation Profiling in Java Mission Control、An Introduction to Protocol Oriented Programming in Swift、API Guides -> Introduction -> Introduction to Android等相关知识的信息别忘了在本站进行查找喔。
本文标签:





