想了解解析OpenSSL程序概念及震惊业界的“心脏出血”漏洞的新动态吗?本文将为您提供详细的信息,我们还将为您解答关于openssl心脏出血漏洞最直接的罪魁祸首的相关问题,此外,我们还将为您介绍关于C
想了解解析OpenSSL程序概念及震惊业界的“心脏出血”漏洞的新动态吗?本文将为您提供详细的信息,我们还将为您解答关于openssl心脏出血漏洞最直接的罪魁祸首的相关问题,此外,我们还将为您介绍关于CentOS 升级 OpenSSL 至 OpenSSL 1.1.0f 版本 <其中有遇到 libcrypto.so 的问题>、CentOS6.5下OpenSSL升级到OpenSSL 1.0.1g、centos7 升级 openssl,openssh 解决漏洞扫描高危、centos7.4 升级openssl环境至openssl-1.1.0c的新知识。
本文目录一览:- 解析OpenSSL程序概念及震惊业界的“心脏出血”漏洞(openssl心脏出血漏洞最直接的罪魁祸首)
- CentOS 升级 OpenSSL 至 OpenSSL 1.1.0f 版本 <其中有遇到 libcrypto.so 的问题>
- CentOS6.5下OpenSSL升级到OpenSSL 1.0.1g
- centos7 升级 openssl,openssh 解决漏洞扫描高危
- centos7.4 升级openssl环境至openssl-1.1.0c

解析OpenSSL程序概念及震惊业界的“心脏出血”漏洞(openssl心脏出血漏洞最直接的罪魁祸首)
详细内容,见 http://www.jb51.net/hack/398231.html
编译命令:
gcc -g -o ssl_server ssl_server.c -I/home/zyk/openssl-1.0.1f/include -L/usr/lib -lssl -lcryptossl_server.c 源代码;
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <netinet/in.h>
#include <sys/types.h>
#include <sys/socket.h>
#include "openssl/bio.h"
#include "openssl/rsa.h"
#include "openssl/crypto.h"
#include "openssl/x509.h"
#include "openssl/pem.h"
#include "openssl/ssl.h"
#include "openssl/err.h"
#define server_cert "./server.crt"
#define server_key "./server.key"
#define ca_cert "./ca.crt"
#define PORT 9876
#define CHK_NULL(x) if ((x)==NULL) exit (1)
#define CHK_ERR(err,s) if ((err)==-1) { perror(s); exit(1); }
#define CHK_SSL(err) if ((err)==-1) { ERR_print_errors_fp(stderr); exit(2); }
int main ()
{
int err;
int listen_sd = -1;
int sd = -1;
struct sockaddr_in sa_serv;
struct sockaddr_in sa_cli;
int client_len;
SSL_CTX* ctx = NULL;
SSL* ssl = NULL;
X509* client_cert = NULL;
char* str = NULL;
char buf [4096];
SSL_METHOD *meth = NULL;
SSL_library_init();
SSL_load_error_strings();
ERR_load_BIO_strings();
OpenSSL_add_all_algorithms();
meth = (SSL_METHOD *)SSLv23_server_method();
ctx = SSL_CTX_new(meth);
if (NULL == ctx) {
goto out;
}
//SSL_CTX_set_verify(ctx,SSL_VERIFY_PEER,NULL);
//SSL_CTX_load_verify_locations(ctx,ca_cert,NULL);
if (SSL_CTX_use_certificate_file(ctx, server_cert, SSL_FILETYPE_PEM) <= 0) {
goto out;
}
if (SSL_CTX_use_PrivateKey_file(ctx, server_key, SSL_FILETYPE_PEM) <= 0) {
goto out;
}
if (!SSL_CTX_check_private_key(ctx)) {
printf("Private key does not match the certificate public key\n");
goto out;
}
listen_sd = socket(AF_INET, SOCK_STREAM, 0);
if (-1 == listen_sd) {
goto out;
}
memset (&sa_serv, ''\0'', sizeof(sa_serv));
sa_serv.sin_family = AF_INET;
sa_serv.sin_addr.s_addr = INADDR_ANY;
sa_serv.sin_port = htons(PORT);
err = bind(listen_sd, (struct sockaddr*) &sa_serv, sizeof(sa_serv));
if (-1 == err) {
goto out;
}
err = listen(listen_sd, 5);
if (-1 == err) {
goto out;
}
client_len = sizeof(sa_cli);
sd = accept(listen_sd, (struct sockaddr*)&sa_cli, &client_len);
if (-1 == err) {
goto out;
}
printf ("Connection from %d, port %d\n",sa_cli.sin_addr.s_addr, sa_cli.sin_port);
ssl = SSL_new(ctx);
if (NULL == ssl) {
goto out;
}
SSL_set_fd(ssl, sd);
err = SSL_accept(ssl);
if (NULL == ssl) {
goto out;
}
/*
printf ("SSL connection using %s\n", SSL_get_cipher(ssl));
client_cert = SSL_get_peer_certificate(ssl);
if (client_cert != NULL) {
printf ("Client certificate:\n");
str = X509_NAME_oneline (X509_get_subject_name (client_cert), 0, 0);
CHK_NULL(str);
printf ("\t subject: %s\n", str);
Free (str);
str = X509_NAME_oneline (X509_get_issuer_name (client_cert), 0, 0);
CHK_NULL(str);
printf ("\t issuer: %s\n", str);
Free (str);
X509_free (client_cert);
}
else
printf ("Client does not have certificate.\n");
*/
err = SSL_read(ssl, buf, sizeof(buf) - 1);
if (err == -1) {
goto out;
}
buf[err] = ''\0'';
printf ("Got %d chars:''%s''\n", err, buf);
err = SSL_write(ssl, "I hear you.", strlen("I hear you."));
CHK_SSL(err);
out:
if (-1 != sd) {
close(sd);
}
if (-1 != listen_sd) {
close(listen_sd);
}
if (ssl) {
SSL_free(ssl);
}
if (ctx) {
SSL_CTX_free(ctx);
}
return 0;
}
CentOS 升级 OpenSSL 至 OpenSSL 1.1.0f 版本 <其中有遇到 libcrypto.so 的问题>
概述:
整体步骤如下:
1.先检查版本
2.进行安装
《安装采用源码安装,然后再做相关的链接指向》
一、检查当前环境
1. 查看当前版本
openssl version 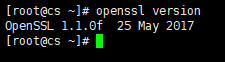
或者使用
yum info openssl 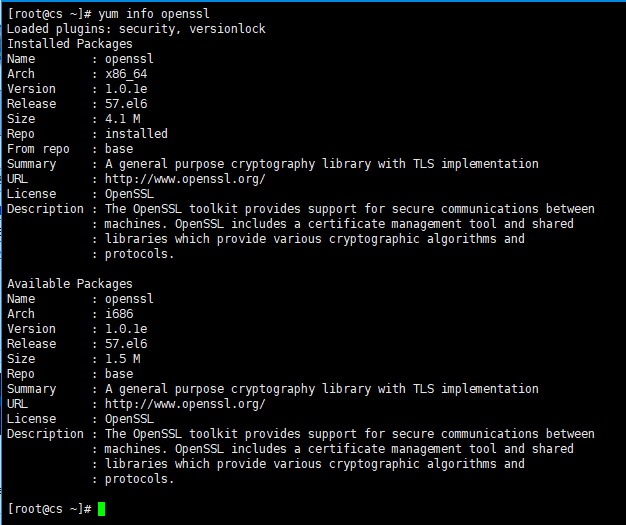
2. 在升级之前检查一下 openssl 的路径
which openssl 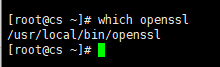
因为需要在升级 openssl 之后,我们需要使用软链接将其链接回此路径
二、准备开始升级安装
1、下载与解压
cd ~
wget https://www.openssl.org/source/openssl-1.1.0f.tar.gz
tar -xzf openssl-1.1.0f.tar.gz2、编译与安装
如果没有安装 gcc 可能会报错,可以直接使用 yum 安装一下 gcc
yum install gcccd openssl-1.1.0f
./config
make
make install3、尝试运行应该会出现下面的这个错误:
/usr/local/bin/openssl version
/usr/local/bin/openssl: error while loading shared libraries: libcrypto.so.1.1: cannot open shared object file: No such file or directory4、下面为相关的解决办法:
创建链接至 libssl
ln -s /usr/local/lib64/libssl.so.1.1 /usr/lib64/
ln -s /usr/local/lib64/libcrypto.so.1.1 /usr/lib64/5、创建链接至新的 openssl
ln -s /usr/local/bin/openssl /usr/bin/openssl_latest6、检查 openssl_latest 的版本号是否是新的版本
openssl_latest version
OpenSSL 1.1.0f 25 May 20177、重命名旧的 openssl 文件名,并且将新的文件名改为 openssl
cd /usr/bin/
mv openssl openssl_old
mv openssl_latest openssl

CentOS6.5下OpenSSL升级到OpenSSL 1.0.1g
# cd /usr/src# wget https://www.openssl.org/source/openssl-1.0.1g.tar.gz -O openssl-1.0.1g.tar.gz
# tar -zxf openssl-1.0.1g.tar.gz
# cd openssl-1.0.1g
# ./config
# make
# make test
# make install
# openssl version(显示的是旧的版本1.0.1e)
执行下面的命令:
# mv /usr/bin/openssl /root/ (或者删除)
# ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
# openssl version
OpenSSL 1.0.1g 7 Apr 2014

centos7 升级 openssl,openssh 解决漏洞扫描高危
准备 telnet留后路
安装telnet-server以及xinetd
[root@bingo ~]# yum install xinetd telnet-server -y
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors.163.com
* epel: mirrors.aliyun.com
* extras: mirrors.cn99.com
* updates: mirrors.cn99.com
Package 2:xinetd-2.3.15-13.el7.x86_64 already installed and latest version
Package 1:telnet-server-0.17-64.el7.x86_64 already installed and latest version
Nothing to do
[root@bingo ~]#- 配置telnet
现在很多centos7版本安装telnet-server以及xinetd之后没有一个叫telnet的配置文件了。
如果下面telnet文件不存在的话,可以跳过这部分的更改
[root@bingo ~]# ll /etc/xinetd.d/telnet
ls: cannot access /etc/xinetd.d/telnet: No such file or directory如果下面文件存在,请更改配置telnet可以root登录,把disable = no改成disable = yes
[root@rhel yum.repos.d]# cat /etc/xinetd.d/telnet
# default: on
# description: The telnet server serves telnet sessions; it uses \
# unencrypted username/password pairs for authentication.
service telnet
{
disable = no
flags = REUSE
socket_type = stream
wait = no
user = root
server = /usr/sbin/in.telnetd
log_on_failure += USERID
}
[root@rhel yum.repos.d]# vim /etc/xinetd.d/telnet
[root@rhel yum.repos.d]# cat /etc/xinetd.d/telnet
# default: on
# description: The telnet server serves telnet sessions; it uses \
# unencrypted username/password pairs for authentication.
service telnet
{
disable = yes
flags = REUSE
socket_type = stream
wait = no
user = root
server = /usr/sbin/in.telnetd
log_on_failure += USERID
}配置telnet登录的终端类型,在/etc/securetty文件末尾增加一些pts终端,如下
pts/0
pts/1
pts/2
pts/3配置之后的显示
[root@bingo ~]# vim /etc/securetty
[root@bingo ~]# tail -5 /etc/securetty
xvc0
pts/0
pts/1
pts/2
pts/3
[root@bingo ~]#启动telnet服务,并设置开机自动启动
[root@bingo ~]# systemctl enable xinetd
[root@bingo ~]# systemctl enable telnet.socket
Created symlink from /etc/systemd/system/sockets.target.wants/telnet.socket to /usr/lib/systemd/system/telnet.socket.
[root@bingo ~]#
[root@bingo ~]# systemctl start telnet.socket
[root@bingo ~]# systemctl start xinetd
[root@bingo ~]# netstat -lntp|grep 23
tcp6 0 0 :::23 :::* LISTEN 1/systemd
[root@bingo ~]#切换到telnet方式登录,以后的操作都在telnet终端下操作,防止ssh连接意外中断造成升级失败
telnet方式登录
一、linux中将openssl升级到1.1.1l
- 下载版本:https://ftp.openssl.org/source/ ,下载最新的1.1.1k版本
- 旧版本地址:https://www.openssl.org/sourc...
将openssl-1.1.1l.tar.gz 上传到服务器
进入openssl-1.1.1.l目录下,编译安装
build
[root@bogon ~]# yum -y install gcc pcre-devel zlib-devel openssl openssl-devel gcc make -y
[root@bogon ~]# ./config --prefix=/usr/local/openssl #指定安装路径
[root@bogon ~]# make && make install #编译安装
- 等待安装完成,执行下面的操作
#备份旧的openssl文件
[root@bogon ~]# mv /usr/bin/openssl /usr/bin/openssl.old
[root@bogon ~]# mv /usr/lib64/openssl /usr/lib64/openssl.old
[root@bogon ~]# mv /usr/lib64/libssl.so /usr/lib64/libssl.so.old
#创建软链接
[root@bogon ~]# ln -s /usr/local/openssl/bin/openssl /usr/bin/openssl
[root@bogon ~]# ln -s /usr/local/openssl/include/openssl /usr/include/openssl
[root@bogon ~]# ln -s /usr/local/openssl/lib/libssl.so /usr/lib64/libssl.so
[root@bogon ~]# echo "/usr/local/openssl/lib" >> /etc/ld.so.conf
[root@bogon ~]# ldconfig -v #显示正在扫描的目录及搜索到的动态链接库
[root@bogon ~]# openssl version
OpenSSL 1.1.1l 24 Aug 2021二、linux中将openssh升级到8.8
https://openbsd.hk/pub/OpenBS...
[root@bogon openssh-8.8p1]# mv /etc/ssh /etc/sshbak
[root@bogon openssh-8.8p1]# ./configure --prefix=/usr/ --sysconfdir=/etc/ssh --with-openssl-includes=/usr/local/openssl/include --with-ssl-dir=/usr/local/openssl --with-zlib --with-md5-passwords
[root@bogon openssh-8.8p1]# make && make install
[root@bogon openssh-8.8p1]# cd
[root@bogon ~]# openssl version
OpenSSL 1.1.1l 24 Aug 2021
[root@bogon ~]# ssh -V
OpenSSH_8.8p1, OpenSSL 1.1.1l 24 Aug 2021
三、配置启动文件
修改配置文件最终为如下内容,其他的不要动
[root@bogon openssh-8.8p1]# grep "^PermitRootLogin" /etc/ssh/sshd_config
PermitRootLogin yes
[root@bogon openssh-8.8p1]# grep "UseDNS" /etc/ssh/sshd_config
UseDNS no
从原先的解压的包中拷贝一些文件到目标位置(如果目标目录存在就覆盖)
(可能下面的ssh.pam文件都没用到,因为sshd_config配置文件貌似没使用它,请自行测试。我这边是拷贝了)
[root@bogon openssh-8.8p1]# pwd
/root/openssh-8.8p1
[root@bogon openssh-8.8p1]# cp -a contrib/redhat/sshd.init /etc/init.d/sshd
[root@bogon openssh-8.8p1]# cp -a contrib/redhat/sshd.pam /etc/pam.d/sshd.pam
[root@bogon openssh-8.8p1]# chmod +x /etc/init.d/sshd
[root@bogon openssh-8.8p1]# chkconfig --add sshd把原先的systemd管理的sshd文件删除或者移走或者删除,不移走的话影响我们重启sshd服务
[root@bogon openssh-8.8p1]# mkdir /root/backupltx
[root@bogon openssh-8.8p1]# mv /usr/lib/systemd/system/sshd.service /root/backupltx/设置sshd服务开机启动
[root@bogon openssh-8.8p1]# chkconfig sshd on
注意:正在将请求转发到“systemctl enable sshd.socket”。
Created symlink from /etc/systemd/system/sockets.target.wants/sshd.socket to /usr/lib/systemd/system/sshd.socket.
[root@bogon openssh-8.8p1]# /etc/init.d/sshd restart
Restarting sshd (via systemctl): [ 确定 ]
[root@bogon openssh-8.8p1]# ssh -V
OpenSSH_8.8p1, OpenSSL 1.1.1l 24 Aug 2021
[root@bogon openssh-8.8p1]# systemctl restart sshd
[root@bogon openssh-8.8p1]#
[root@bogon openssh-8.8p1]# netstat -lntp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:5000 0.0.0.0:* LISTEN 30045/uwsgi
tcp 0 0 10.87.2.201:170 0.0.0.0:* LISTEN 9018/ssh
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 1657/mysqld
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 1832/dnsmasq
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 36299/sshd: /usr/sb
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1303/cupsd
tcp 0 0 10.87.2.201:248 0.0.0.0:* LISTEN 24147/ssh
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1599/master
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 30045/uwsgi
tcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTEN 57973/./zabbix_agen
tcp 0 0 0.0.0.0:2020 0.0.0.0:* LISTEN 26008/uwsgi
tcp 0 0 10.87.2.201:9988 0.0.0.0:* LISTEN 45084/ssh
tcp 0 0 10.87.2.201:11301 0.0.0.0:* LISTEN 27176/ssh
tcp6 0 0 :::22 :::* LISTEN 36299/sshd: /usr/sb
tcp6 0 0 :::23 :::* LISTEN 5794/xinetd
tcp6 0 0 ::1:631 :::* LISTEN 1303/cupsd
tcp6 0 0 ::1:25 :::* LISTEN 1599/master
tcp6 0 0 :::10050 :::* LISTEN 57973/./zabbix_agen
[root@bogon openssh-8.8p1]# ssh -V
OpenSSH_8.8p1, OpenSSL 1.1.1l 24 Aug 2021

centos7.4 升级openssl环境至openssl-1.1.0c
升级openssl环境至openssl-1.1.0c@H_301_2@
升级openssl环境至openssl-1.1.0c
1、查看源版本
[root@zj ~]#openssl version -a
OpenSSL 1.0.1e-fips 11 Feb 2013
2、下载 openssl-1.1.0c.tar.gz
最新版本可以在这个网站下载:
https://www.openssl.org/source/
wgethttp://www.openssl.org/source/openssl-1.1.0c.tar.gz
3、更新zlib
yum install -y zlib
4、解压安装
tar zxfopenssl-1.1.0c.tar.gz
cdopenssl-1.1.0c
./config shared zlib
make
make install
mv /usr/bin/openssl /usr/bin/openssl.bak
mv /usr/include/openssl /usr/include/openssl.bak
ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
ln -s /usr/local/ssl/include/openssl /usr/include/openssl
echo “/usr/local/ssl/lib” >> /etc/ld.so.conf
ldconfig -v
5、查看是否升级成功
[root@zj ~]#openssl version -a
解决openssl: error while loading shared libraries: libssl.so.1.1: cannot open shared object file: No such file or directory错误
问题在Centos7上编译安装openssl后,运行openssl version出现如下错误:openssl: error while loading shared libraries: libssl.so.1.1: cannot open shared object file: No such file or directory这是由于openssl库的位置不正确造成的。解决方法:在root用户下执行:ln -s /usr/local/lib64/libssl.so.1.1 /usr/lib64/libssl.so.1.1ln -s /usr/local/lib64/libcrypto.so.1.1 /usr/lib64/libcrypto.so.1.1
升级openssl环境至openssl-1.1.0c
1、查看源版本
[root@zj ~]#openssl version -a
OpenSSL 1.0.1e-fips 11 Feb 2013
2、下载 openssl-1.1.0c.tar.gz
最新版本可以在这个网站下载:
https://www.openssl.org/source/
wgethttp://www.openssl.org/source/openssl-1.1.0c.tar.gz
3、更新zlib
yum install -y zlib
4、解压安装
tar zxfopenssl-1.1.0c.tar.gz
cdopenssl-1.1.0c
./config shared zlib
make
make install
mv /usr/bin/openssl /usr/bin/openssl.bak
mv /usr/include/openssl /usr/include/openssl.bak
ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
ln -s /usr/local/ssl/include/openssl /usr/include/openssl
echo “/usr/local/ssl/lib” >> /etc/ld.so.conf
ldconfig -v
5、查看是否升级成功
[root@zj ~]#openssl version -a
解决openssl: error while loading shared libraries: libssl.so.1.1: cannot open shared object file: No such file or directory错误
问题在Centos7上编译安装openssl后,运行openssl version出现如下错误:openssl: error while loading shared libraries: libssl.so.1.1: cannot open shared object file: No such file or directory这是由于openssl库的位置不正确造成的。解决方法:在root用户下执行:ln -s /usr/local/lib64/libssl.so.1.1 /usr/lib64/libssl.so.1.1ln -s /usr/local/lib64/libcrypto.so.1.1 /usr/lib64/libcrypto.so.1.1
今天关于解析OpenSSL程序概念及震惊业界的“心脏出血”漏洞和openssl心脏出血漏洞最直接的罪魁祸首的介绍到此结束,谢谢您的阅读,有关CentOS 升级 OpenSSL 至 OpenSSL 1.1.0f 版本 <其中有遇到 libcrypto.so 的问题>、CentOS6.5下OpenSSL升级到OpenSSL 1.0.1g、centos7 升级 openssl,openssh 解决漏洞扫描高危、centos7.4 升级openssl环境至openssl-1.1.0c等更多相关知识的信息可以在本站进行查询。
本文标签:









